A threat intelligence analyst spotted a post in a community forum about "1,800 vulnerable and deflated Pulse VPN" accounts on Tuesday, August 4.
The list includes usernames and passwords as well as IP addresses for Pulse Secure VPN enterprise servers. ZDNet got a copy of the list and found more than 900 Pulse VPN" accounts, half of what the hacker's post indicated.
According to an exclusive report, the media outlet was assisted by KELA, a threat intelligence firm, which gave them a copy of the Pulse VPN list. The company also seeks the help of various cyber-security sources to verify the report's authenticity.
A well-known Russian-speaking Threat Actor shared details of over 1800 IPs vulnerable to the latest Pulse CVEs.
Timestamps on the folders or scan dates show that the list was created between June 24 and July 8. The threat intelligence analyst Bank Security who specialized in financial crime shared the list on Twitter. He said on his tweet that a popular Russian-speaking Threat Actor shared information about more than 1800 IPs that were compromised by the latest Pulse CVEs.
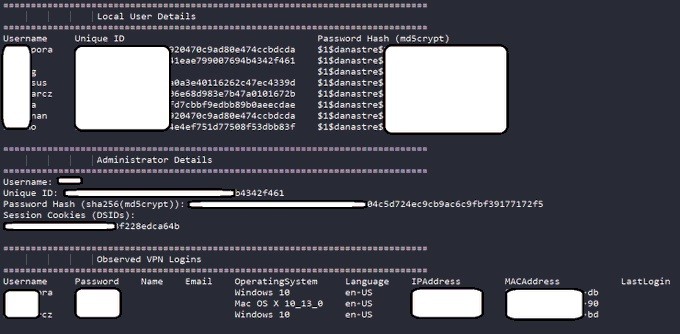
A well-known Russian-speaking Threat Actor shared details of over 1800 IPs vulnerable to the latest Pulse CVEs. For each IP the actor shared many details including user & administrator clear-text credentials. Big Banks and notable organizations are on the list.
PATCH NOW! pic.twitter.com/QqyPBG17Mq — Bank Security (@Bank_Security) August 4, 2020
Bank Security made interesting observations about the content of the list. The list includes Pulse Secure VPN servers IP addresses and firmware version, SSH keys for each server, admin account details as well as local users and password hashes.
The review also found VPN session cookies and last VPN usernames and cleartext passwords. According to the security analyst, all the Pulse Secure VPN servers in the list were running a firmware version that is exposed to CVE-2019-11510, where a remote attacker can send a unique URI to release a file reading vulnerability.
In a nutshell, one of the DBs used by cyber criminals to sell access to various companies through Pulse Secure vulnerabilities has been shared. Some of the victims are categorized by type and revenue to maximize the sale. — Bank Security (@Bank_Security) August 4, 2020
He believed the hacker scanned the entire IPv4 address space for Pulse Secure VPN servers and then accessed the systems using an exploit for the CVE-2019-11510 vulnerability. The attacker then dumped server details including usernames and passwords and collected all data in one central source.
Read also: [BEWARE] Chinese Government Uses Malware? US Government Warns Public to be More Alert
Unpatched Pulse Secure VPN serves
Meanwhile, a US-based threat intelligence company Bad Packets that issued a scan in August 2019 for vulnerable Pulse Secure VPN with the CVE-2019-11510 vulnerability. It appears that 677 companies on the list did not repair the vulnerability, so they are included in the recent attack.
"Of the 913 unique IP addresses found in that dump, 677 were detected by Bad Packets CTI scans to be vulnerable to CVE-2019-11510 when the exploit was made public last year," co-founder and chief research officer of Bad Packets told ZDNet.
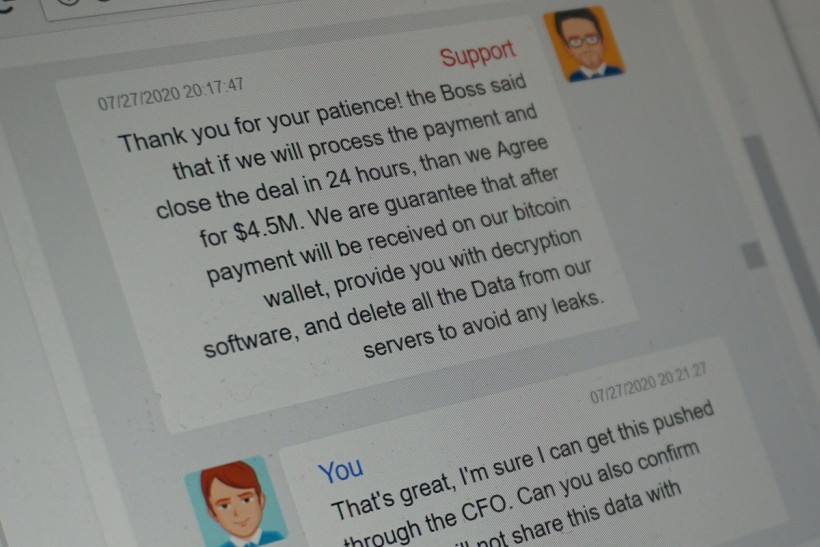
Part of the payment negotiations between ransom -seeking cybercriminals - marked "Support" - and a representative of travel giant CWT - marked "You" is seen in this photo taken in Washington, D.C., U.S., July 30, 2020. Picture taken July 30, 2020.
Worse, the list has been shared on a hacker forum where ransomware gangs like NetWalker, REvil (Sodinokibi), Avaddon, Lockbit, Exorcist, and Makop. These groups have their threads on the said forum where they recruit developer members and customers.
According to VpnTesting, Most of the ransomware gangs invade corporate networks by leveraging network devices like Pulse Secure VPN servers. They usually demand huge ransom demands from the affected companies.
Bank Security urged affected companies to immediately patch their Pulse Secure VPNs and change their passwords to avoid cyber criminals from utilizing the leaked credentials to control devices and access their internal networks. Since Pulse Secure VPN servers are usually used as gateways to access corporate networks, allowing staff to remotely connect to internal apps, it also permits hackers to the company's entire internal network when compromised.
This article is owned by Tech Times
Written By CJ Robles
* This is a contributed article and this content does not necessarily represent the views of techtimes.com









