
It is not uncommon for companies and organizations to employ several security software tools to protect their networks, devices, and digital assets. From antiviruses to firewalls, packet sniffers, and penetration testing, organizations need different security solutions to address different needs and settings.
According to a cybersecurity market report featured on Cybercrime Magazine, organizations worldwide are expected to spend around $170.4 billion for security solutions in 2022. This amount will be spent on a host of security products including malware protection software, personal identity theft protection services, and post-breach solutions.
The use of multiple best-in-class cybersecurity tools, however, does not guarantee optimum protection. For some, it can even add to the risks. Inexperienced IT teams that are unfamiliar with new security tools and complicated security ecosystems may not be getting the best out of the products they have in place. Worse, the improper use of these tools may create more vulnerabilities.
Cybersecurity centralization
Centralizing an organization's cyber defenses does not necessarily mean using security products from a single vendor, although it is an option. The idea is to unify all security controls, tools, or systems so they can be managed better and to ensure optimum protection.
Audry Agle, Vice President at The First American Corporation, shared some insightful notes about security governance centralization in a piece for CSO Online. "Centralized governance is generally most efficient as resources can be leveraged in a cost-effective manner across the organization, thereby limiting duplication of effort and better-utilizing talent and tools." she wrote.
Changes in the cybersecurity landscape create compelling reasons to centralize. As security firm Cyrebro's 2021 cybersecurity prediction says, multi-cloud environments and the work-from-home arrangement are most likely to continue even after the pandemic. The firm also expects an accelerated adoption of extended detection and response (XDR) solutions and the growing popularity of managed service service providers (MSSPs). These can result in networks that involve multiple security solutions, which can become too complicated, underutilized, redundant, or inefficient.
Optimal cybersecurity is a must as businesses contend with the rapidly growing volume and increasing sophistication of cyber attacks. One of the best ways to achieve optimum defense is centralization, something possible with the help of a reliable security platform.
Unified security operations platform with Cyrebro
As mentioned, it is not necessary to switch to a single security solutions provider to achieve cybersecurity centralization and unification. There are third-party solutions that make it possible to bring all security software tools and systems together. An excellent example of this is Cyrebro, an online Security Operations Center (SOC) designed to integrate the management of all security events.
Cyrebro serves as a cloud-based cybersecurity central command that brings together all security events to enable strategic monitoring and proactive intelligence. It lays claim to the distinction of being "the first online security operations platform that helps manage the ongoing burden of security operations." Additionally, it facilitates faster responses to security events, especially in cases of successful attacks so that an organization can promptly implement all the necessary mitigation, remediation, and recovery solutions.
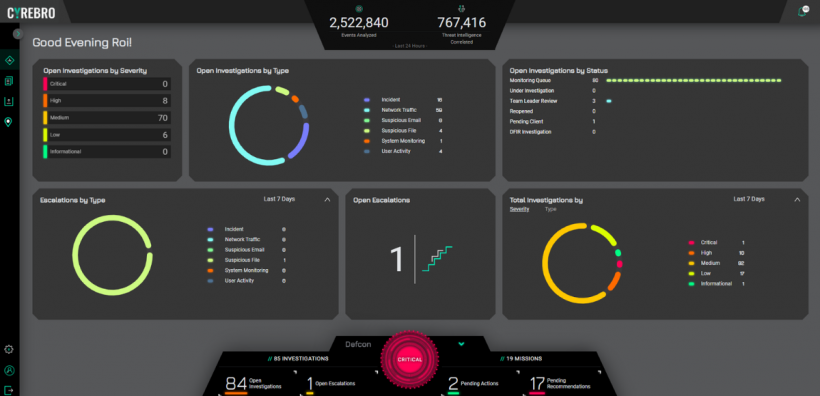
Cyrebro provides a single dashboard to monitor all security event information in an organization as collected by various security solutions. It presents an easy to understand report with alerts and indicators to guide IT teams about existing vulnerabilities, threats, attacks, and the recommended actions to take.
How can a third-party solution unify all security tools?
Designed to be a plug-and-play platform, Cyrebro can integrate all security events. It can connect to virtually all of the existing security tools used by organizations. It is built to be technology-agnostic to make sure that it works with any kind of application, operating system, or software in general.
So how does the integration process work? Cyrebro provides a log source connectivity wizard, which is under the Reporting System Wizard interface. This simplifies the process of integrating all security solutions with the platform. It provides step-by-step instructions on how to go about with the integration of different security applications.
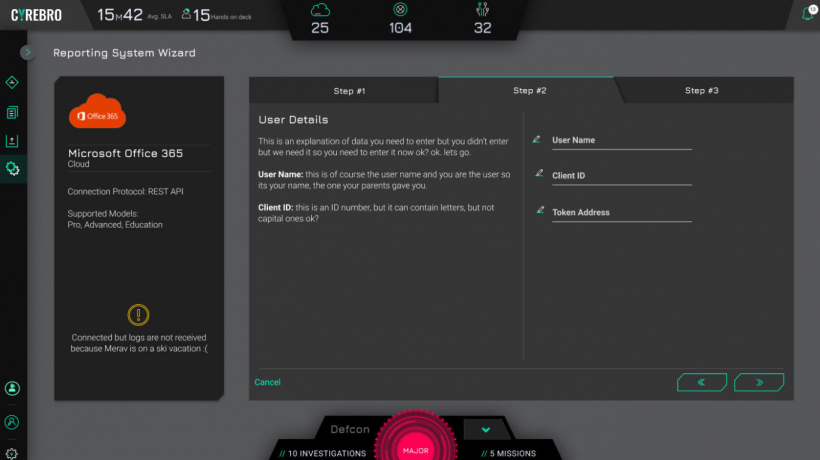
Regardless of the antivirus, firewall, VPN, EDR, WAF, or other cybersecurity solution used, Cyrebro provides a unified system for monitoring and responding to threats. It works with the security tools from PT Telecom, FireEye, Trend Micro, Awake, Hillstone, Snort, McAfee, Gigaman, IronDefense, Panda Endpoint Protection, Micro Focus, Comodo, Webroot, Security Onion, and many other security providers.
The benefits of centralization
Unifying all security controls through Cyrebro provides the main advantage of comprehensive visibility and transparency. It allows security teams to see all critical incidents across business operations. Cyrebro presents organized threat alerts with indications for their respective type, severity, and status. It also provides notifications for incident escalation when it comes to complex cases.
Comprehensive security visibility makes it possible to have strategic threat monitoring and enhanced threat intelligence. These benefits, in turn, result in rapid incident response, security optimization, and better digital security forensic investigation.
Cyrebro continuously monitors all security activities and generates an actionable list of security investigations. It presents everything that is happening in an organization's network security in real-time, so security teams can address threats as soon as possible and prevent or radically minimize disruptions.
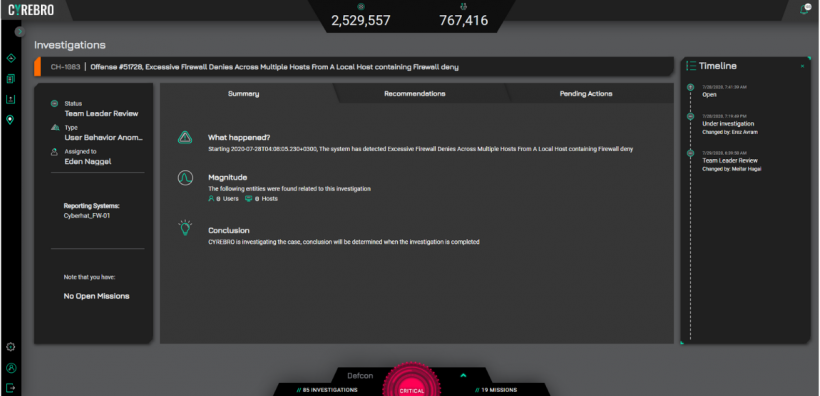
Cyrebro presents detailed security investigations that include information on the assets impacted, immediate risks, status, and recommended actions. The threats or attacks are identified, analyzed, and described with great precision through cross-organization learning.
Aside from tracking threats and attacks in a network, Cyrebro also allows users to see which security solutions are online and working for an organization's defense at any given moment. It can track endpoints worldwide including the laptops, desktops, mobile devices, and servers that connect to a company's network of digital resources.
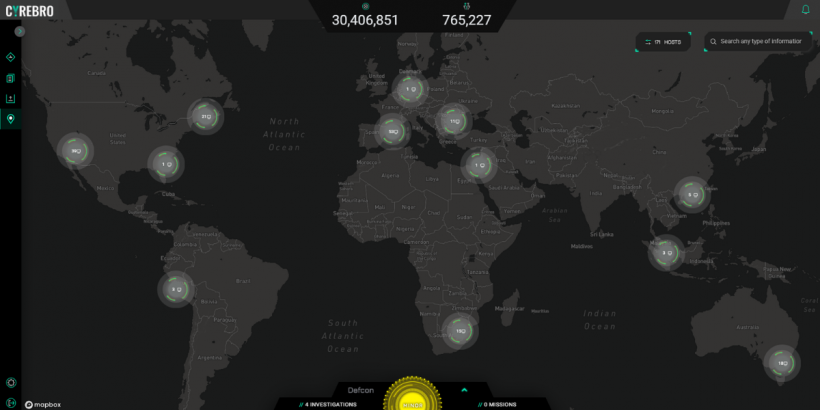
Taking centralization a notch higher, Cyrebro has a Hosts Map feature that displays the geographic location of an organization's web hosts along with information on their coverage, state of connectivity, and relevant security alerts.
Enhanced convenience and protection
Aside from the log that facilitates quick and easy integration, Cyrebro also comes with a report generator. This feature allows users to create monitoring reports with a few clicks. The reports can contain all the relevant data of ongoing or resolved security investigations, charts, and summaries of all security events, which can provide valuable insights on an organization's cybersecurity state. The reports can show not only the number of cases but also their level of severity and escalation of investigations undertaken.
By choosing a well-designed platform, centralizing security solutions does not have to be complicated and limited to those who have advanced cybersecurity experiences. It can even open the possibility of optimization.
With comprehensive security visibility and real-time logs, security analysts can have a better way to scrutinize the effectiveness of their current setup. Once they identify vulnerabilities or security solutions that do not appear to be working the way they are intended, they can introduce tweaks, adjustments, or replacements to improve the overall security posture.
Cybersecurity centralization is not only for large corporations. It is also applicable to small and midsize businesses as well as micro-enterprises. Cyrebro is designed not only for micro-businesses, SMBs, and enterprise users. It also has use cases for managed security service providers (MSSPs).
In summary - how centralization enhances protection
As Cyrebro's slogan maintains, centralization takes cybersecurity "from chaos to clarity." By integrating various security solutions in one cloud-based system, security teams gain a significantly better view of their security status, making it easy to identify weaknesses, monitor threats, respond to security events, and conduct forensic investigations. All of these can be done without the need to install new software and worry about updates and maintenance.
Cyrebro says that it can dramatically reduce the time it takes to investigate cyber attacks from days to hours and even minutes. This alone is reason enough to consider security centralization given that 93 percent of attacks compromise systems within a few minutes.
* This is a contributed article and this content does not necessarily represent the views of techtimes.com









