Passwords can be easily stolen, cracked, and compromised through brute force attacks, phishing, data breaches, or a hacker's use of malware. Research shows that nearly 50% of attacks caused by threat actors to enterprises are attributed to stolen credentials, according to the Verizon 2022 Data Breach Investigations Report.
Passwordless authentication minimizes the risks associated with passwords. It refers to a group of identification methods verifying a user's identity without a password. It provides secure access for enterprises, requiring less user interaction during the login process to improve an organization's end-user experience and security posture.
List of Password Management Software
| Password Management Softwares | |
|---|---|
 | LastPass |
 | Bitdefender |
 | LogMeOnce |
 | Tenorshare |
 | Nordpass |
What are the benefits of going passwordless?
Going passwordless does not guarantee full-proof protection from cyberattacks. However, enterprises that utilize passwordless authentication instead of traditional password-based authentication are less likely to witness security incidents attributed to credentials. It also decreases support costs, reducing the burden on support teams and other operational costs spent on password resets and troubleshooting.
Passwordless authentication is also easier to set up, simplifying user onboarding, which results in an overall better user experience. With minimal impact on users' productivity, enterprises may see an increase in conversion rates since it eliminates the frustration of the average user with traditional password-based authentication.
Outlined below are the top 5 best passwordless authentication software systems in 2023:
1 SSH PrivX

Overview
SSH Communications Security (SSH) is a cybersecurity company specializing in securing communications between people, applications, networks, and systems, including privileged access and credentials management.
This helps companies build a proactive defensive cybersecurity posture to reduce the risk of breaches and lets organizations grow in the digital world without constant worry about attacks and leaks.
SSH is trusted by over 5,000 customers worldwide, including Fortune 500 companies, government agencies, financial institutions, retailers, and top manufacturers.
Adopting the principle of Defensive Cybersecurity, SSH is proactive in building protection to mitigate the risk of breaches, especially those related to credentials. By identifying vulnerabilities and weaknesses beforehand, enterprises can eliminate potential attacks well in advance.
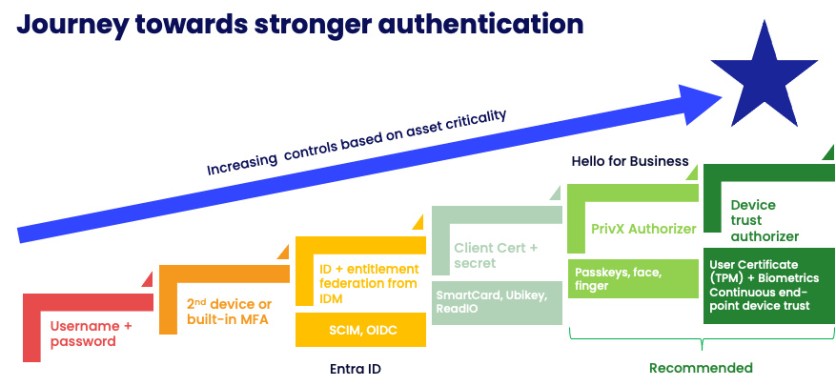
The company's PrivX, a hybrid privileged access management (PAM) solution, can enable strong identity authentication depending on the customer's needs by using any of the following options:
- Traditional username + password
- 2nd device or built-in multi-factor authentication (MFA) for ID check
- Federation of user IDs and entitlement from Identity Management Systems (IDM)
- User certificates (like smart cards, Ubikeys, FIDO2) combined with a secret
- Using FIDO2-based PrivX Authorizer with passkeys, face or finger recognition (recommended for critical sessions)
- User certificate + Biometrics, coupled with continuous end-point device trust monitoring (recommended for critical sessions)
Verifying the user through biometric authentication, validating the device, time & location for the session, and linking the verified user with the right role for access results in a passwordless and keyless Zero Trust Authentication. The validation happens invisibly and automatically without the user having to take any extra steps since the combination of user ID, device ID, location, time and behavior creates a robust verification. In addition, the validity of the session is continuously monitored, so that if the device status changes (for example, the antivirus goes offline), the session is automatically stopped.
Alternatively, PrivX can link to solutions like Microsoft's Entra ID and can rely on the authentication provided by them. PrivX is particularly strong in handling superuser and poweruser access to mission-critical targets, like credit card databases, production environments, network devices, domain controllers or industrial targets. The solution minimizes the risk of passwords, keys, and other leave-behind credentials as a highly automated privileged access management solution. It is built for hybrid and multi-cloud environments, quantum-safe connections, and any combination of password vaulting, rotation, and passwordless authentication to support traditional as well as modern environments
When using passwordless authentication, the software uses short-lived tokens for access. All the secrets needed for the session are baked in the token, but the user never sees or handles them: they just get immediate, role-based Zero Trust access to the right target for the right duration with the right level of access. The token expires automatically within minutes, leaving zero credentials to be managed. It makes privileged access management easy, productive, and secure while decreasing complexity and cost.
By combining passwordless authentication and phishing-resistant MFA, SSH ensures only authorized users and secure devices can access privileged accounts, applications, databases, network devices, or industrial targets. This approach defends organizations against modern identity and access-related threats.
The solution changes the field of identity and access management and privileged access management as organizations move away from static perimeter-based cyber defenses to a Zero Trust model, making cybersecurity fit for borderless ecosystems where there are no safe zones. It also enables organizations to monitor, verify, and control system access by automating access control processes and simplifying user identity verification.
The SSH approach creates a cybersecurity solution that makes access management more convenient, eliminating traditional SMS messages or forced password rotation solutions. It provides access in a highly automated manner based on the user's profile, regardless of the nature of the connection.
Features
Centralized Access
PrivX centralizes access to mission-critical targets under a single pane of glass, from servers, multi-cloud hosts, data centers, web applications, and more. Only privileged users get to see the available targets, ensuring no entry for threat actors.
Automate Access
PrivX automates access based on the given roles of each user. It synchronizes with directory services and maps the existing identity groups to specific access privileges. Utilizing role-based access control eliminates the need to modify the access privileges every time there are changes in users or user groups.
Track, Record, and Monitor Privileged Session
PrivX displays an audit trail so admins can track, record, and monitor privileged sessions, regardless of the required protocol. The passwordless authentication works smoothly on any modern browser, even without plug-ins or a command line interface.
Bird's Eye View of All Accounts
PrivX provides a bird's eye view of all accounts. From root, domain, service, local, application, and system accounts, the passwordless authentication software displays each type of account operating on-premises and cloud server estate. It also updates changes in real time through automatic scanning.
Fast Deployment & Scaling
SSH offers fast deployment and scaling of its passwordless authentication software. Clients have the option to install PrivX on-premises or on the cloud. The privileged access management solution is also available as Infrastructure-as-a-Code to be installed on an AWS account or deployed in containers.
Save Time, Money, and Nerves
PrivX saves time, money, and nerves spent on password and credential management by accelerating the daily work of privileged users and minimizing the complexity of privileged access management. This improves the operational efficiency of enterprises, leading to a greater ROI and low TCO.
When using SSH passwordless authentication, there's no need to rotate, vault, manage, or even worry about leave-behind credentials like passwords or authentication keys. PrivX makes access management more convenient and efficient for enterprises, mitigating insider and third-party risk while accelerating operations and productivity with zero-trust authentication methods.
2 LastPass

Overview
LastPass is a password manager tool that stores, secures, and auto-fills user passwords. It offers a password vault containing credentials, secure notes, and sensitive information. It provides compatibility with any device and browser, seamlessly working across everything, regardless of the operating system.
Features
LastPass frees users from password pains and risks with passwordless vault login. This sophisticated system offers quick access through various passwordless authentication methods. Users must verify their device once with a master password, and then they can access their vault with their preferred verification method.
Going passwordless means fewer password resets. LastPass removes password barriers by giving users instant access to applications and credentials they need most. Its passwordless authentication also provides a protection layer for the user's device, biometrics, and FIDO2-certified authenticator.
With FIDO2 authenticators, LastPass reduces the risk of phishing and password theft. It utilizes industry-leading authentication standards such as W3C's Web Authentication specification and FIDO Client to Authenticator Protocol, replacing the master password with a more secure and faster login experience.
LastPass offers its Authenticator app, fingerprint or face ID, and hardware key for passwordless authentication. While it requires possession-based credentials to operate, the tool is easy to set up and use, even free to download.
3 Duo Passwordless

Overview
Duo Pasworldess utilizes passkeys and platform authenticators to secure application access without passwords. Its passwordless authentication minimizes the risk surface and administrative burden associated with credentials while improving the user experience. It is available on specific plans such as Duo Premier, Duo Advantage, and Duo Essentials.
Features
Duo Passwordless relies on Duo Single Sign-On with Active Directory Authentication. Duo SS includes all of the product's deep security features. Enterprises with an existing SSO identity provider can still connect the current SAML identity provider to Duo SSO.
The passwordless authentication software supports a diverse set of end-user authenticators and passkeys, from Windows Hello (Windows), Touch ID (Mac OS), Face ID/Touch ID (iOS), biometrics, FIDO2 security keys, or the Duo Push authentication request. It also supports browsers like Chrome, Safari, Edge, and Firefox.
Duo Passwordless offers automatic fallback to password login with 2FA in scenarios when passwordless isn't available. With a comprehensive view of user accounts, admins can view or delete users' platforms and roaming passwordless authenticators from the Duo Admin Panel. Admins can also set policies around which apps and user groups can access passwordless authentication as an option, simplifying the rollout of the authentication method.
With minimal setup time, multiple device and OS compatibility, and seamless integrations, Duo Passwordless boosts user productivity and reduces IT by providing frictionless access, self-service, and remediation for users that strengthen their security posture.
4 Salesforce Identity

Overview
Salesforce Identity streamlines user access with a single login. It removes friction around authentication, thus improving the customer experience and preventing customer churn. Users simply need to enable single sign-on, social sign-on, or passwordless login with a few clicks.
It removes barriers that slow employees down and maintains robust security controls to maintain the security posture, ensuring only authenticated users can access company resources, such as external productivity tools or internal services. Its passwordless authentication methods include email, time-based one-time password, physical U2F security key, and Salesforce Authenticator.
Features
Salesforce Identity drives productivity by providing a single sign-on for all cloud, mobile, and on-premises apps, lessening the operations of IT and making entry seamless for a mobile workforce. It also provides a better view of customers on every channel. Admins can grant access to customers through their social media credentials to simplify the identity verification process.
Salesforce Identity also integrates with on-premises enterprise directories, extending their value through simple synchronization to enable single-sign and delegated authentication. It delivers enterprise-class security while providing a smooth user experience. With two-factor authentication, admins can verify to secure apps and data from risks of insider threats.
Salesforce protects users' identities and data integrity through Salesforce Identity. Enterprises can leverage its fast and convenient passwordless authentication method to reduce the complexities and security risks associated with passwords.
5 Microsoft Entra ID

Overview
Microsoft Entra ID is the new name of Azure Active Directory. It is a cloud identity and access management solution with comprehensive capabilities. It prevents identity takeover in real time, automates access governance, simplifies identity verification, and secures access to any application for customers and partners.
Features
The passwordless authentication software of Microsoft features app integrations and single sign-on. Enterprises can connect their workforce to all apps from any location with any device in one dashboard through one set of credentials. It also offers multifactor authentication methods such as texts, biometrics, or OTPS to increase an organization's security posture against breaches.
Microsoft Entra ID also features conditional access, an intelligent policy engine to help organizations monitor users' activity when accessing corporate resources. It displays real-time signals, including user context, device, location, and session risk information, so admins can determine whether to allow, block, or limit access, even restrict access completely for vulnerable and compromised devices.
Equipped with advanced machine learning, Microsoft Entra ID also automatically detects and remediates identity-based risks and unusual user behavior, preventing insider threats and other forms of credential theft. The passwordless authentication software also strengthens the security of privileged accounts. It offers a time-based and approval-based activation to prevent misuse or unnecessary access to company resources.
With a unified admin center, the Microsoft passwordless authentication software centralizes all multi-cloud identity and network access solutions in one place. It offers a seamless user experience while safeguarding confidential company and user information.
Conclusion
Going passwordless allows enterprises to avoid risks related to traditional password-based authentication. Choose among the top five best passwordless authentication software providers and gift users with a seamless, friction-free entry. With a stronger security posture and reduction of operational costs, businesses can thrive, resulting in higher productivity, lead conversions, and, eventually, higher ROI.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




