
Israel-based malware disarm firm odix recently raised another $2.1 million in round A funding from private angel investors leaded by Efraim Landa.
This brings the company's total funding to $6 million. The funding allows odix to innovate, expand its reach, and make enterprise-grade security accessible to more users. This comes as a welcome development especially in the malware protection segment.
Today's malware variants have become quite complex and are now capable of executing processes such as providing remote access; hijacking computing resources and devices; and exfiltrating, encrypting, and destroying data. They are capable of disguising themselves within legitimate files and even mutating to avoid detection.
odix uses content disarm and reconstruction (CDR) as an approach to mitigate and neutralize modern malware threats. CDR essentially deconstructs files in order to screen for and remove malicious code. Files are then reconstructed to make them usable unlike with conventional antiviruses and anti-malware solutions wherein users are forced to quarantine or fully delete the infected files.
We recently sat down and spoke with odix Dr. Oren Eytan who shared his thoughts on cybersecurity outlook for the year and how his company looks to contribute to the space.
The growing malware threat
The World Economic Forum considers cyberattacks to be among the top global risks today, viewed in the same light as natural disasters and climate change. Security experts all claim that cybersecurity threats are bound to grow even more rampant this year.
Malware, in particular, has been making headlines recently. Trojans, which are designed to give hackers access to systems and steal credentials and sensitive information from targets, continue to be spread and be active. LokiBot, for instance, has recently been reported to be disguised as a video game launcher. New ransomware variants have also been spotted in the wild. Instead of simply encrypting files and holding decryption keys for ransom, they are now able to exfiltrate data prior to encryption.
For Eytan, enterprises should worry about such threats since they are able to bypass most existing security systems. Malware attacks can also originate from sources that organizations might consider safe like cloud and software as a service (SaaS) services. He considers increasing cloud adoption as something that organizations have to keep an eye on.
"I believe that the consumption growth in cloud and SaaS services by companies raises new areas of cybersecurity threats," Eytan says. Most small to medium-sized businesses (SMBs) and even enterprises are not aware of SaaS business apps vulnerabilities and relay on the vendors basic security they provide. Sometimes you must have additional security layers to protect your company data assets even in basic apps like corporate email."
CDR as an approach to defending against malware
Defending against these new malware can be a challenge as conventional methods can fall short in dealing with the malware threat. Endpoint protection, such as antiviruses, is easily circumvented by cleverly disguised malware. Sandboxing requires users to deliberately test files in an isolated environment. Considering most work files are sent and received through various channels like email and web downloads, sandboxing each file that enters the network can become a cumbersome task.

Odix kiosk and booth in action
"CDR is different from antivirus or sandbox methods that scan for threats, detect a subset of malware, and block files. CDR verifies the validity of the file structure on the binary level and disarms threats regardless if they are known or unknown. With CDR, all malware, including zero-days, are prevented and the user gets a safe copy of the originally infected file," Eytan explains.
CDR's ability to deal with both known and unknown malware is also a game-changer. Legacy solutions like antiviruses typically need to have update virus definitions to deal with recently known malware. Unfortunately, this means that users are left vulnerable until their solutions providers are able to provide these necessary updates. Enterprises that wish to protect themselves from file-based attacks that use unknown malware would greatly benefit from CDR.
Solutions for enterprises
As a malware disarm solution, odix is designed to help enterprises cover their bases. The company's lineup of products can perform CDR on email attachments, files in transit over the network, and even removable storage. It also provides an application programming interface (API) that allows CDR to be integrated with other enterprise applications.
"Our approach is to offer easy to deploy solutions for file based attacks. As files can infiltrate organizations in multiple channels, our offering include several files sanitizations' modules or plugins accordingly ensuring quick deployment and service activation," says Eytan.
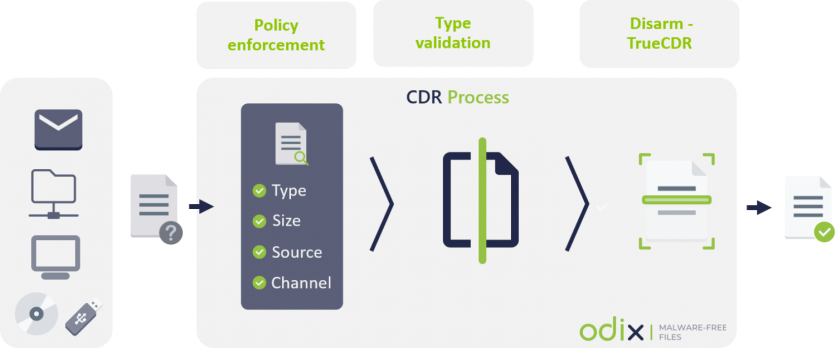
How odix works
Enterprises are pressured to strengthen their cybersecurity posture as they remain popular targets for attackers. Cyberwarfare, in particular, has gained much attention due to the escalation of political conflict to start the year. State-sponsored advanced persistent threats (APTs) have been reported to be actively targeting not only governmental facilities but also industrial enterprises such as energy, utilities, and manufacturing.
"The increasing attacks on critical industrial targets are a cause for worry. Successful attacks on such facilities can harm civilian life. As such, there's a need for the highest level of security in industrial companies. They have to comply with standards and regulations. Some sectors have specific cyber processes to follow. odix understands that fully well, and we designed some of our solutions to meet the compliance requirements. For example, we help US-based energy companies like Vistra Energy and Dominion Energy to meet the NERC CIP standards," comments Eytan.
odix's Kiosk solution, which serves as a dedicated station to perform CDR on removable and portable storage devices, is finding use in industrial facilities. Most control systems are kept offline for security purposes. Transferring data to and from these systems often requires removable storage devices. The Kiosk can help ensure that these devices are kept malware-free.
An eye toward the future
odix's successful funding round underscores the need for growth and innovation in the segment. The company looks to use the fresh capital for business growth. odix plans to expand its market share in the US and to penetrate new markets in Europe by allocating more funds to sales and marketing. Product-wise, the company has also launched the beta version of its new Office 365 native Outlook plugin and looks to introduce more Office 365 services in the future.
While odix's product lineup is targeted more toward larger enterprises, the company also acknowledges the need to make its services available downmarket and provide solutions for smaller organizations.
"SMBs are definitely more vulnerable to cyber threats compare to large enterprises; in fact, over 60 percent of the attacks target SMBs. We understand that SMBs need to better protect themselves but with minimal deployment and ongoing operation investment. Our new software as a service (SaaS) service for Office 365 users is perfectly suited to provide a zero deployment and operation solution to SMBs. In fact, the development of our new is cosponsored by the European Commission through its Horizon 2020 project. The EC awarded a €2-million grant to odix a few months ago. Aside from the grant, it's a great recognition for odix technology and the direction we target for our services. I guess we are doing something good," Eytan concludes.
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




