Fonix Ransomware operators have decided to shut down their operations and have subsequently released the master decryption key for all of their victims for free, allowing the victims to retrieve their files.
Fonix Ransomware Shuts Down
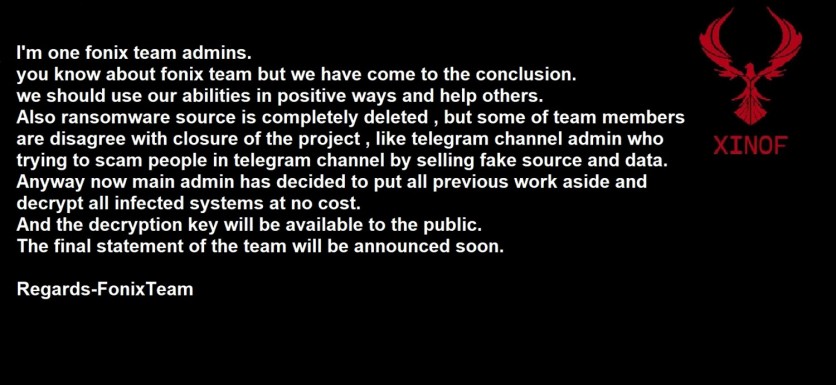
According to BleepingComputer, a Twitter user claiming to be a Fonix ransomware admin shared a post on the account, saying that the group was shutting down and that they decided to use their abilities in "positive ways and help others."
Nevertheless, the said Fonix admin has also shared that not every one of them is happy with the group shutting down.
The admin claimed that one of the admins of the group who was running a Telegram channel and scamming other people on the platform "by selling fake source and data."
The news outlet said that some of the Fonix admins can join a new ransomware group or create their own separate operations following the shutdown, so it is still important for people to remain vigilant online.
The admin behind the Twitter account also said that since they are shutting down, they have also decided to give away the master decryption key to all of their victims for free, which enables them to retrieve the files lost when they were attacked by the group and that it will be available to the public.
Moreover, the admin said that the team's final statement will also be released.
The Master Decryption Key Released
As promised, a separate tweet by the same Twitter handle linked people to the master decryption key, which is a RAR archive named "Fonix_decypter.rar" that contains both the decryptor and the master private decryption key.
Nevertheless, it's not exactly the decryptor tool that will decrypt your entire computer yet.
As it turns out, the tool is an admin tool instead, which the ransomware gang would send to its victims and decrypt a few encrypted files, just to show that they can indeed unlock their devices.
The news outlet decided to try the decryption tool sent by the Twitter account, and while it does work by decrypting one file at a time, it has a confusing set of instructions and is apparently prone to crashing, but the master keys appear to work, although only for certain Fonix ransomware versions.
But it does appear that Emisoft's decrypter will be able to work on all versions of the Fonix ransomware, such as .FONIX, .Fonix, .XINOF, and .repter encrypted file extensions.
No ETA for the Decrypter
The admin handling the Twitter account has sent out another tweet telling its followers to send them a private message on the platform if they needed help with using the tool, but they have not said when the exact decryptor will be sent out.
However, if you were a victim of the Fonix Ransomware group, a solution may be available soon.
For those who are not aware, ransomware is a sort of cybercrime wherein the attackers would encrypt your entire computer and in exchange for the decryption key that would return it to normal, they would ask for money.
This article is owned by Tech Times
Written by: Nhx Tingson
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




