
Ever since the early days of computers, cybercriminals have been creating malware to compromise the internal systems and files of electronic devices. This insidious threat often goes unnoticed unless proper scanning measures are in place. Malware possesses the ability to steal sensitive information from users when triggered by malicious software hidden within clickbait ads or files downloaded from untrusted sources.
The risks associated with malware are significant. Once activated, it can spread throughout the device, corrupting stored data and causing widespread damage. Additionally, criminals can exploit the compromised system to gain unauthorized access to users' personal information and launch threats that demand payment or ransom in exchange for restoring device security.
In some cases, the risk materializes in the form of persistent and intrusive advertisements that cannot be eliminated without employing dedicated malware analysis tools. To assist users in combating this menace, here are the top five recommended malware analysis tools as of 2023:
1 ANY.RUN

ANY.RUN is a cloud-based interactive sandbox for DFIR/SOC investigations with an intuitive interface. Unlike automatic sandbox solutions, ANY.RUN enables users to interact directly with malware samples in a safe, private, and real-time virtual machine environment. This entails a faster and more precise identification of threats and extraction of all the data essential for thorough incident response and prevention.
Whatever you analyze with ANY.RUN, it delivers exceptional results at all times, detecting and analyzing targeted cyberattacks, zero-day vulnerabilities, and advanced malware with unknown signatures in mere seconds.
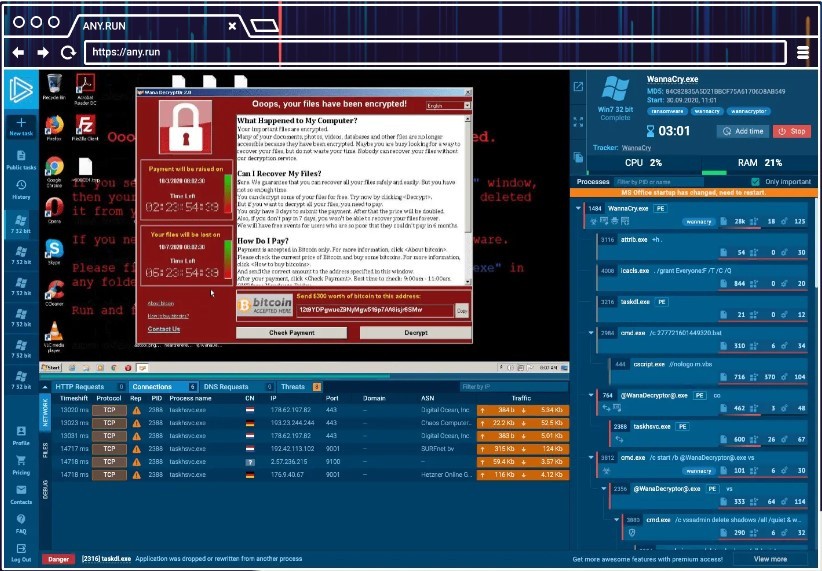
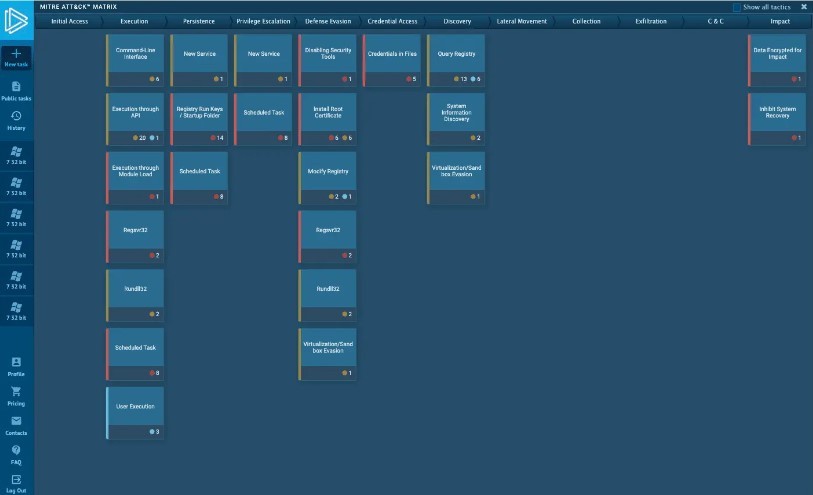
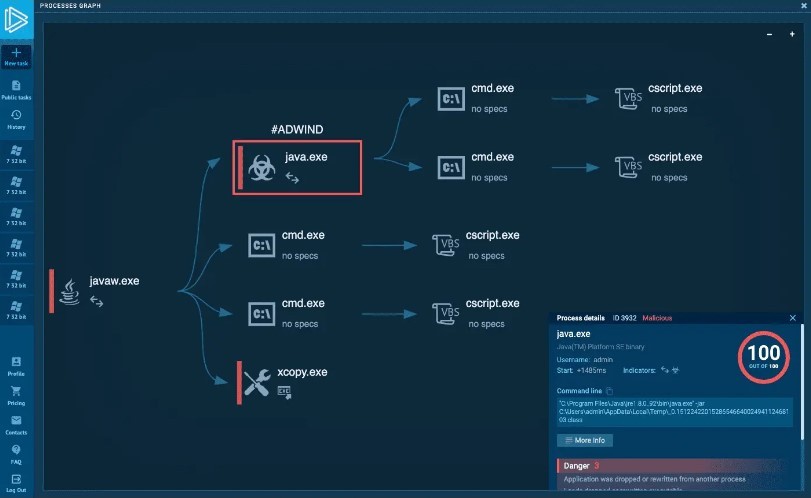
ANY.RUN's large selection of emulation parameters allows you to fine-tune your analysis, including by picking a preferred Windows version and locale. It collects indicators of compromise (IOCs), lets you investigate attackers' TTPs with the MITRE ATT&CK matrix, and produces a process graph documenting malicious programs' behavior. On top of that, it generates comprehensive yet easy-to-understand reports on malware activity, saving analysts plenty of time and effort.
Most importantly, an entire team of analysts can use the service to work on samples together. ANY.RUN also has a public database of 6,200,000 malware samples submitted by users from around the world.
ANY.RUN boasts an extensive range of features that greatly benefit analysts and organizations. Here are some of the major advantages of the platform:
Extended time for analysis. Certain types of malicious software may need a little more time and effort to start their harmful actions. ANY.RUN grants this extra time, allowing you to click around, reboot your VM, and explore the file at length with no constraints.
All Windows versions. The service features all the most common Windows versions, including 7, 8, 10, and 11. By altering the OS version, you can gain insight into different attack tactics employed by the malware and better understand potential security breaches.
Private tasks. You have the ability to remove your tasks or choose to make them visible to others. Plus, you can share your analyses exclusively with those you trust.
Teamwork. The tool facilitates collaboration, allowing several team members to analyze the same file.
Improved resource management. You no longer need to spend countless hours waiting for results. With its user-friendly interface, ANY.RUN is accessible to analysts of all levels. The first batch of relevant data gets generated in 5 seconds, making your operations more efficient and effective than ever.
Thanks to the 14-day free trial, you can experience the value of ANY.RUN firsthand. Simply submit a request and one of ANY.RUN's managers will get in touch to grant you access. Please note that this offer is exclusively available to those with business emails.
ANY.RUN is trusted by thousands of satisfied customers from dozens of industries, which is evidenced by numerous reviews.
2 Coro Cybersecurity

Recognized by industry leaders, Coro offers a different approach to ensuring security. Coro focuses on intelligent automation so IT teams can focus on enabling business for their respective companies. Fueled by artificial intelligence, Coro's platform automatically identifies and remediates the most known cyber threats and vulnerabilities.
Coro has built its platform to provide holistic security protection. It is considerably easy to use and affordable. By utilizing AI, Coro can anticipate the risk and identify and address the issues automatically, allowing companies to save resources. Coro protects organizations from the following:
malware & ransomware
phishing
hacking and access control
insider threats
data loss and governance
Coro eliminates the need to purchase multiple systems or to manually conduct malware analysis because, across all endpoints, users, data, and cloud applications, Coro is proactive and holistic in its protection. Coro only alerts the user when necessary. With 1-click resolve, users can easily take action on the malware, making mitigation of security as convenient as possible.
Coro is available to use through a 14-day free trial. It offers free threat detection, monitoring of users, cloud apps, emails, and a 3-month audit trail. For users who want to access its 1-click resolve feature, Coro currently offers the Coro Annual + Cyber Advisor at a discounted price of $8.99 per month and Coro Edge at $12.99 per month, both billed annually.
3 Intezer Analyze

Intezer aims to improve and optimize the daily tasks of a security operations center (SOC), incident response teams, and threat intelligence teams by equipping them with automated technology to stay ahead of threat actors. This allows more efficient decision-making for detection, response, and ongoing support for constant threat hunting.
With Intezer Analyze, users and organizations get a virtual autonomous SOC that resolves about 89% of false positive alerts and investigates 98% of alerts automatically, providing actionable remediation recommendations. Intezer Analyze offers the following:
Alert Triage: This enables round-the-clock monitoring and deep investigation of endpoints and email alerts while automatically resolving false positives.
It also works to reverse engineer suspicious files and processes and contextualizes alerts with recommended actions and threat analysis.
Response: This offers actionable IOCs and clear instructions for remediation. It contains behavior rules that hunt and resolve additional infections.
Hunting: This feature enables Intezer Analyze to search for stealthy attacks like APT and cybercrime campaigns that common malware analysis tools do not detect easily. It ensures tracking threat actors for an ongoing update of detection opportunities.
All these features are automated into the Intezer Analyze. Intezer also allows integrations with other malware analysis tools like CrowdStrike, SentinelOne, or the built-in Windows Defender. Through integrations, users can make the most out of the security measures they have in place to identify, investigate, and remove malware and other kinds of viruses infiltrating their devices.
Intezer is also free to use for a trial period of 14 days, while its other premium features are only accessible when they purchase either Triage or Respond.
4 ESET Protect Complete

Established in 1992, ESET is a global digital security company offering multiple malware analysis tools. They have protected millions of customers and companies in its 30 years. The company is only concerned with one goal: protecting customers and businesses for a better future.
Highly regarded by its partners and independent analysts, ESET is part of Google's App Defense Alliance, where it serves to protect the Google Play Store for millions of smartphone users. Throughout the years, ESET has gained multiple awards and titles for its work as a cybersecurity company, like being a Champion in the Canalys Global Cybersecurity Leadership Matrix or Top Player in Radicati's 2021 Endpoint Security Market Quadrant for four consecutive years.
ESET has released several protective and malware analysis tools that cater to the average user's personal use, home, small office, and businesses. The ESET Protect Complete contains nearly all premium features required for complete, multilayered protection across devices. With full disk encryption, advanced threat defense, mail security, and vulnerability and patch management, the Protect Complete secures endpoints, cloud applications, and emails of businesses.
Businesses and users are secured due to the advanced technology built into their tools. They contain ESET LiveSense technology that offers multiple layers of protection for one's cyber security and is powered with machine learning expertise and a cloud reputation system. ESET owns the world's most capable cyber threat prevention, detection, and response platform.
In the market alone, ESET is unparalleled in the number of users and businesses it has protected worldwide, amounting to over a hundred million and over four hundred thousand, respectively. ESET's products are costly, yet consumers are assured of getting their money's worth with its advanced technological security measures for multiple operating systems.
5 Wildfire of Palo Alto Networks

Global cybersecurity leader Palo Alto Networks continues to deliver innovations that enable secure digital transformation through its products like WildFire. It is the industry's largest cloud-based engine made for malware analysis and protection.
Powered with machine learning and crowd-sourced intelligence, WildFire instantly prevents up to 95% of unknown malware variants without interfering with business productivity to protect and secure organizations. Below are its key features:
Proactive and accelerated security: Built as the largest engine, companies benefit from the speed of WildFire, which can perform 60x faster compared to other tools for malware analysis.
Real-time prevention: WildFire can analyze twice as many unique malware samples per month as the average malware sandbox engine. With its built-in machine learning, this product can stop rapidly changing malware immediately, especially threats that move through a computer's firewall, with no cloud analysis needed nor loss of user productivity.
Prevention at scale: Due to its cloud-based architecture, WildFire enables malware protection in seconds across all networks, endpoints, and cloud locations once it's detected by this largest customer network for cybersecurity, consisting of 85,000 organizations.
Organizations benefit from WildFire of Palo Alto Networks, reducing the risk of security breaches by 45%, which leads to $6 million in efficiency due to the decreasing resources allocated for investigation, response, and imaging time. Users may contact Palo Alto Networks for its price, though the company allows anyone a free trial of 30 days to test one of the best tools for malware analysis in the market.
Consider these top five best tools for malware analysis. From sandboxes to cloud-based services and a unified platform, these tools offer varying features yet similar functionalities that ultimately detect and remove any malware. Organizations and average users can surely keep themselves protected from any harmful threat with these highly recommended best malware analysis tools.
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




