Link previews pop out whenever people send URLs and website addresses on social messaging applications such as Apple's iMessage, Facebook Messenger, and WhatsApp, showing the actual content or a snippet of what to expect. According to online security researchers, link previews potentially endanger people in user data breach and exposure from malicious entities online.
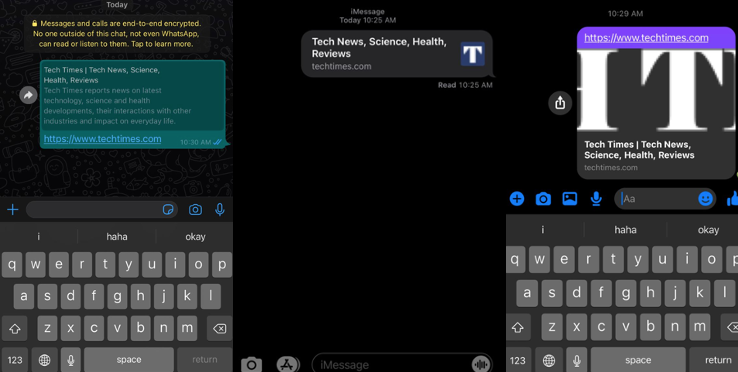
Most of the social messaging applications available in the market offer the feature that is practical and helpful to know what website and content one was sent and will soon open. The function intends to help a user with a "security protection" before opening links and falling for what it brings.
Link Previews: How Did it Become Dangerous?

However, link previews are now perceived as "double-edged swords" that can also bring potential harm and breach on one's data and risk exposure from hackers who latch themselves on innocent links. According to 9 to 5 Mac, security researchers were able to prove this via studying modern link previews.
Talal Haj Bakry and Tommy Mysk share their findings and discovery that both iOS and Android platforms which use the social messaging applications are at risk for a potential data breach. The security researcher's duo found out that there are malicious entities that can latch itself on links alone, leading to several information being accessible even without opening the links.
The researchers argue that an application automatically open links in the background to fetch the "metadata" or the preview from each website's link that is sent through the messaging apps. This reason alone compromises the integrity and security of a user, even without opening links.
Read Also: Facebook Cloud Gaming Launching With Free-to-Play Games for Android!
Link Previews: Security and Data Breach at Risk

According to Tommy Mysk's blog post, several messaging applications are contributing to the security breach and data exposure without the actual intention of the apps to do so. Social messaging applications can go as far as leaking IP addresses, exposing links despite using end-to-end encryption services and silently downloading "gigabytes" of data in the background.
The researchers were able to summarize and identify applications to have different kinds of approaches whenever a link is sent through messages:
- Sender Generates the Preview - The bloggers explain that the first option is the safest one despite having a link preview because it shows that the sender trusts the link sent. Messaging apps under the first approach includes Apple's iMessage, Viber, and WhatsApp.
- Receiver Generates the Preview - This second approach is the most "at risk" approach by messaging applications because it protects the sender and puts the receiver in danger through link preview. Apps that use this approach include Reddit's chat, even goes as far as sending the IP address of the receiver.
- Server Generates the Preview - The last approach is skeptical because both sender and receiver do not know what they are in, but it avoids the IP leaks compared to the previous one. Apps with this method include Messenger, Discord, Hangouts, Instagram, LINE, LinkedIn, Twitter, and Zoom.
The third approach, Server Generating Preview, has some concerns over its functionality. The approach does not precisely protect from IP leaks but avoids it. Moreover, this approach downloads data and file from the servers that opened or generated the link, thus leaving the app and phone with data from the website.
Mysk and Haj advise people to avoid generating preview links from the website to avoid data breach and exposure altogether. Some links have malicious codes hidden within them and are potentially dangerous for the app data, which contains all user information about the owner.
Related Article : 21 Android Apps Spotted Containing Adware Malware: Total of 7 Million Downloads Already
This article is owned by Tech Times
Written by Isaiah Alonzo
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




