The San Francisco 49ers just got hit by a ransomware attack from a group that calls themselves "Blackbyte."

According to The Register, the attackers claim to have stolen important corporate data about the NFL franchise, and are threatening to publish it to the wider web for all the world to see. Initially, they've already posted around 300 MB of stolen files on their publicity site on the dark web.
Some of the data allegedly include critical finances involving the NFL team. ABC News says that Blackbyte has posted a series of files titled "2020 Invoices," which likely shows incoming and outgoing financial transactions performed by the team during the 2020 season. But aside from posting the data they stole, the hackers don't seem to have made any explicit demands from the team.
Considering how the franchise is among the most valuable and profitable in the entire league (it was valued at around $4.18 billion last year), the presence of their financials on the web could be troublesome.
In an answer to the hack, the 49ers have now alerted the authorities and "third-party cybersecurity firms" to deal with the situation. Their initial findings reveal that the incident doesn't seem to involve any system outside of their network, like ticket sales.
This ransomware attack comes after the FBI, in collaboration with the US Secret Service, issued a warning implicating the Blackbyte group by name, reports ESPN.

In the warning, the feds claimed that Blackbyte has already infiltrated and compromised several American and foreign businesses since November 2021. Among the ransomware group's targets were three "critical" sectors of the United States' infrastructure.
The 49ers ransomware attack is relatively small, but it sets a dangerous precedent early this year. Already, a Fortune 500 company has already been targeted by ransomware hackers last month, further reinforcing the fact that no one is completely safe from a breach.
How The Ransomware Attack On The San Francisco 49ers Happened
Much of the "how" in this situation lies in Blackbyte's operational tactics. As per the advisory from the Feds, the group uses an executable file of the same name to leave a ransom note in every directory that features encryption. They include a .onion site in the same ransom note (a .onion suffix means it's on the dark web) which contains directions on how to pay the ransom.
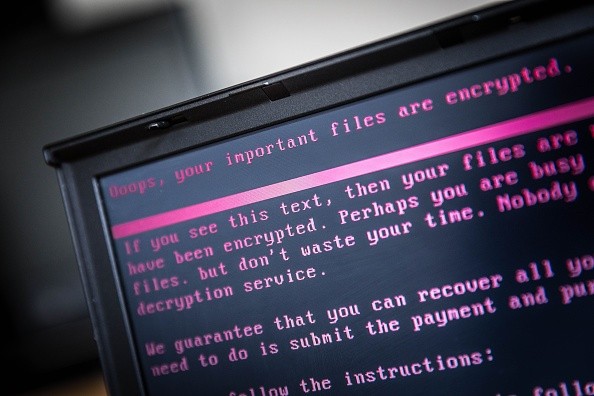
Other victims of the hacker group claim that they also use a well-known vulnerability in the Microsoft Exchange Server to breach their targets' networks.
But until an official reveal is made, the San Francisco 49ers ransomware attack doesn't seem to have any mention of a ransom demand-the very nature of ransomware in the first place. However, it might just be a matter of time before BlackByte makes their demands, mainly due to the money they could get from an extremely valuable sports franchise like the 49ers.
For more news like this, check back right here at Tech Times.
Related Article : Ransomware Hackers Are Looking To Gain Insider Help In Companies They Target--Hitachi ID Report
This article is owned by Tech Times
Written by RJ Pierce
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




