
Hackers need access to phones for various fraudulent activities including stealing banking app data for stealing money, user data including photos for identity theft by creating duplicate certificates and gaining access to several potential targets through contacts. If the question - How to remove a hacker from my iPhone troubles a user after witnessing suspicious activities, this article will cater to all their questions.
Understanding threat to one's iPhone security to remove a hacker from an iPhone.
By gaining access to third-party software, a hacker can gain access to an iPhone which is otherwise fairly secured with strong device controls and certificates. Hence, updating the device as soon as one sees a notification is critical for the safety of one's iPhone. Automatic software updates that need no manual interaction are also helpful.
There are several tools and hackers that meet to launch cyber-attacks against one's iPhone. Some of them are as follows:
Exploiting a vulnerability in the software of the iPhone or apps installed in it.
Unintentionally installing malware on the device after clicking on a link in a fraudulent message.
Brute-force attacks when a hacker tries several common passwords such as abc123, qwerty, and welcome123 to login to the device.
Exploitation after hacking an iPhone.

After a hacker gains access to an iPhone, they may try various cybercrimes to fulfill their intention. Any user who has data, cryptocurrency, and/ or that offers a pathway to enter another target's device, can be targeted by hackers.
They can steal classified data stored in the iPhone, record the camera content, and calls besides microphone audio, among other things. They can leverage the access to launch a DoS attack, ransomware attack, espionage, etc.
To secure one's iPhone from threats that do not need to have physical access to it, one can follow specific steps to mitigate risk. Individuals must also be aware of common cybersecurity news which can be perused in cybersecurity magazines, cyber news, threat intelligence reports on news publications, and so on.
How to remove a hacker from my iPhone
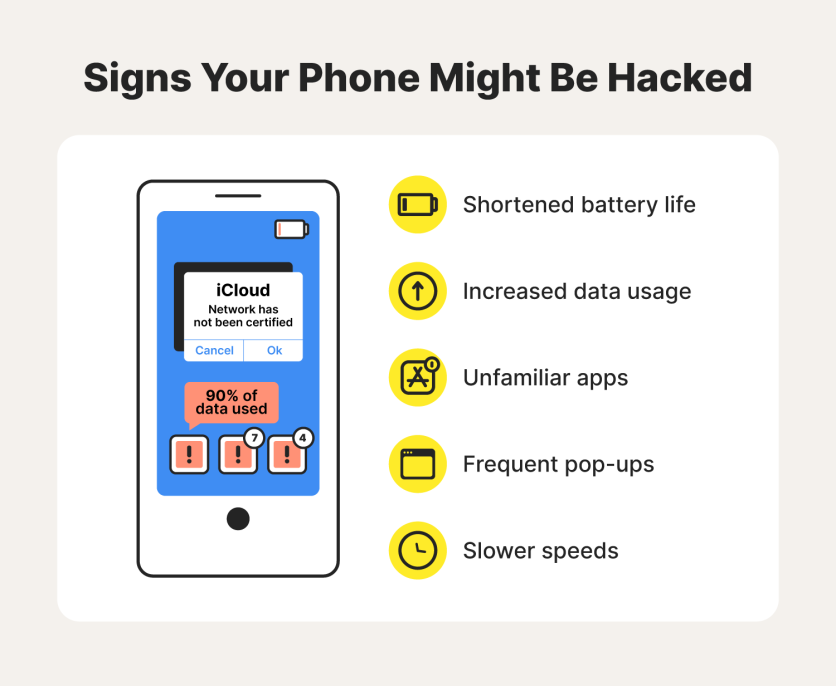
There are suspicious activities that can help confirm a hacking including seeing new apps and admins reflect on the device or the battery getting exhausted sooner than usual. Hackers often run arbitrary codes remotely and install malware that may take up more charge and heat the device in some cases.
A hacker can be removed temporarily, however, for complete assurance that they won't regain access to the once-infected iPhone, several diligent measures must be taken.
These are the steps to remove a hacker from the iPhone -
1. Turn the internet and Wi-Fi off to at once to have the hacker lose connectivity. Since hackers rely on internet connectivity to stay connected to the device remotely, it is the first step to discourage them. Take the phone to the nearest police station or the cybercrime branch for investigations.
2. Format the device with a factory reset which will delete every account created by the hacker on the device to access stored data. However, it will also leave the phone blank to its previous state when it was purchased. Users can sync the stored data from iCloud if backups were made. Try not to back up all the files after discovering suspicious activities. Required data can be backed up by individually selecting them. Yet, it cannot be confirmed that the hacker did not have access to iCloud.
3. Remove apps downloaded outside of the app store including photo editing apps, games, dictionaries, etc.
4. Change the device password and username in all accounts to remove a hacker from your iPhone. To remember the password, one can try slight variations in each of them.
5. Opt for multi-factor authentication to log in using the phone or a newly created email, preferably on another device. This is so the hacker does not know the new credentials and accounts. Soon after getting the OTP on the account, permanently delete the messages.
6. Run the antivirus on the device including all the files and folders and delete all the flagged content.
7. Remove suspicious apps including Telegram which is often used by hackers to forward their cybercrime.
8. Remove recent home screen widgets that can be accessed without a password. One can click on edit to remove it.
9. Create a passcode for the device storage by opening Settings and then adding a passcode using the Touch ID & Passcode option.
10. Install security tools for Ad-blocking like Purify, malware protection and opt for VPN while using the internet.
There can never be a device that cannot be secured more with prudent usage and a better understanding of cyber risks. To remove a hacker from your iPhone, one can stay up-to-date by cybersecurity news that offers updated information.
Older versions of apps and security measures for the same will not remove a hacker from the iPhone. Hence, being ready with the latest threat intelligence reports can help identify hacking attempts before it takes place.
ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




