1. Introduction and Definitions
We live in a world where digitization, automation, and connectivity have become the heart of every organization, business, infrastructure, state, and country. Digital Transformation has been playing a major role in the economic and industrial development of countries. Digital infrastructure has become the most important pillar for a scalable economy. For all major economies in the world, digital infrastructure is a lifeline and the only method for the sustainability of population and economic prosperity.
The next generation of industrial revolution, also defined as Digital Transformation or Industry 4.0, is taking shape. It is changing the everyday lives of citizens and businesses in one of the most structured manners. The intention is to achieve well-defined applicability of digitization for critical aspects of the life of citizens and businesses. It is evident that the United States is leading the change and looking forward to trillions of dollars in economic growth. Healthcare, emergency response systems, critical infrastructure, mass manufacturing, autonomous robotics, and defense systems of the United States will go through changes for future scalability and efficiency. Digital Transformation is founded on Cloud infrastructure proliferation and IOT-based mechanization towards the industrial revolution. The United States and other progressive countries would be competing against each other to gain superiority in those verticals and reap the advantages of being the most advanced economies.

Any setback to digital infrastructural growth would mean huge losses to the country or impact the superiority of the country. As the world is fighting this economic battle for digital transformation, multiple issues related to the security of the digitized world must be addressed by aspiring nations. Digital transformation will change our lives for the better, but at the same time, this phenomenon also suffers critically due to system vulnerabilities.
One of the biggest dangers to Digital Transformation in the United States is Denial of Service attacks (DoS) or Distributed Denial of Service Attacks (DDoS). The extent of damage caused by these attacks can be compared to the impact of Weapons of Mass Destruction (WMD). Therefore, we will term it a Digital Weapon. Let us start by understanding the basics of DoS (Denial of Service) and DDoS (Distributed Denial of Service) attacks. A common unit to measure the size of a large attack is its bandwidth in Terabits per second (Tbps or approximately a trillion bits per second).
2. Security Threats to Digital Transformation
Threats to Digital Transformation can be mainly categorized into three high-level categories:
Threat to Digital Data
Threat to Compute and Control Systems
Denial of Service attacks against control systems and infrastructure
These categories can be subdivided further, but that is not the scope and intent of this discussion.
2.1 Threat to Digital Data
Data is the foundation of Digital Transformation. However, the same data can be used for destructive intents, including for illegitimate financial gain. Digital transformation would require strong data protection security measures that are deterministic and highly effective in terms of data controls. Data suffers from two major types of attacks—data theft and ransomware. Both of them have seen a sharp rise from International Actors against the businesses and the Government of the United States of America. The emerging biggest threat to data is the possibility of massive DDoS attacks on the data systems, which would severely cripple the businesses and governmental operations due to lack of data.
2.2 Threat to Compute and Control Systems
The compute systems for large-scale financial computation and business controls are major targets of attackers and hackers. Not only does it provide financial gains, but it can also severely hurt the financial businesses and the confidence in the systems. Threats to control systems are majorly focused on gaining control of the systems of critical importance to create disruption. These types of attacks may inflict financial or strategic harm to the systems and businesses. By hacking and gaining control of financial institutions or banking systems of vital importance, the attacker can cause major financial havoc to the United States. On the other hand, strategic attacks can include hijacking control systems for emergency response systems, major power grids, power generation stations, air traffic control, or even major defense systems and strategic controls. DDoS attacks on such systems of vital importance mean making these systems unavailable for operations. Even a few seconds of disruptions in these systems amount to significant damage to the economy.
2.3 Denial of Service Attacks Against Infrastructure and Control Systems
Introduction
A Denial of Service attack is a method of attack where the target system is deliberately overwhelmed with fake tasks due to which the target entity cannot perform the functions it is designed for. It makes the target entity incapable of providing part or all of its intended services or functions. The severe form of DoS attack can even make the target entity completely incapable of service. Hence, the term "Denial of Service" was coined. DoS attacks are designed to bring down control elements of large critical systems. Such attacks render the whole critical system non-functional. What makes it even more dangerous is that, unfortunately, DoS attacks are practically unsolvable problems. One system or set of systems of attack together can overwhelm a critical system of finite bandwidth and capacity within minutes. Therefore, no matter how much bandwidth and capacity is provided to a business or control system, there is always a possibility of outsmarting it.
The problem is most severe in all the network-connected entities due to exposure and visibility on the internet. Even in protected networks, such DoS attacks can be induced by insider threats or other unprotected devices.
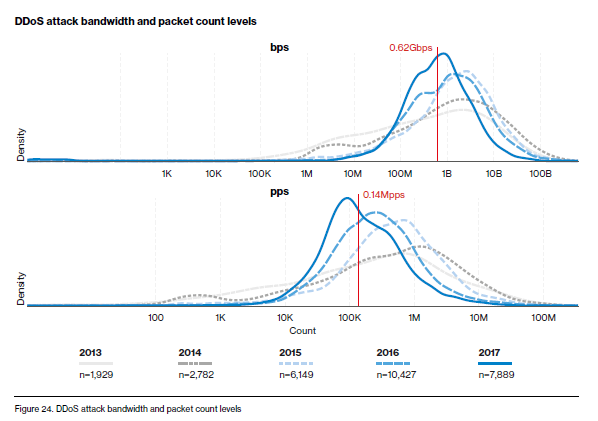
As per the analysis, there has been a rise in the number of DDoS attacks of sub-terabits per second bandwidth. Usually, they last for a short time. As per Verizon's security report of 2018, in one year alone, a total of 21,409 DDoS attacks were counted with certainty. Significant consideration should be provided to the mathematics of simultaneous attacks from a large number of sources. For example, a simultaneous attack by a billion mobile devices on a single target can be as disastrous as an attack by a single supercomputer of one petaflop computing bandwidth.
A DDOS attack is an attack on a server or network caused by flooding of traffic utilizing multiple compromised computer systems. In this case, a target is attacked from many locations at once instead of being attacked from one location. DDOS adds multiple advantages:
The attacker can leverage a huge volume of machines and compute resources to cause a massive disruptive attack
It is extremely difficult to stop multiple machines causing the attack, rather than merely one machine.
It is very difficult to detect the attacking party as they are disguised behind many compromised systems.
This attack renders the real request either slow or no response at all due to a potential shutdown. The question arises: how does an attacker manage to get multiple sources to partake in the attack? The answer is malicious software. The attacker distributes malicious software over the internet via different channels like email attachments, websites, etc. When computer owners accidentally click or open such malware-injected channels, the malicious software gets installed on their computers without them actually knowing about the infection. Such computers, along with an army of other infected computers, are recruited to perform a DDOS attack. This army of infected computers is called a Botnet. We are not talking about a few computers, 100s or 1000s of computers spread across the globe. All the infected computers are controlled by the central main attacker and can perform actions as instructed by the controller. In most cases, the attacker can schedule a date and time for the DDOS attack to be conducted. All the machines part of the Botnet follows the instruction and hit the target with the attack at that specified time. This is also termed a Synchronized Denial of Service attack. This attack could last for minutes, hours, or days, and it completely depends on the attacker.
Why DDoS?
DDoS attack generation is one of the most inexpensive in terms of resource requirement. Many forms of DDoS attacks have already been automated. DDoS is fast approaching weapons-grade due to the multiplication of bandwidth, duration of attack, and difficulty in mitigation.
DDoS are difficult to detect and mitigate due to some of the following reasons:
Attackers leverage a large number of machines and compute resources to cause a massive disruptive attack.
The huge bandwidth of DDoS attacks can overwhelm monitoring systems.
It is extremely difficult to stop or control multiple machines causing the attack.
It is challenging to detect the attacking party as they are disguised behind many compromised systems.
The obvious question here is, how can someone gain control of so many systems to generate simultaneous attacks? The fundamental modus operandi is to push malicious software that looks benign onto those systems. This task can be done in multiple ways, but once infected, the systems can be directly or indirectly controlled by the attacker.
With the effect of simultaneous synchronous DDoS, not only can the bandwidth of the attack be multiplied, but the extent of the damage it can generate is also multiplied. Therefore, weaponizing the DDoS in various forms is equivalent to derivatives of WMD, except that the DDoS can attack the target with much more precision than the WMD and can inflict much more targeted harm to economies.
Along with being very inexpensive to multiply in bandwidth and devastation, DDoS is also being delivered in various forms. Some of them are very difficult to identify due to camouflage, whereas some of them are very difficult to mitigate. At the smallest form factor, the delivery system could be through mobile devices and can be easily multiplied, exploiting a large number of end users. The most complex form could actually be hijacking the satellite bandwidth in upstream or downstream transponders. It would not be a surprise that some of our satellite systems are already owned or mounted with malware that can hijack and convert them into massive-scale DDoS delivery systems.
"Cybercriminals launched approximately 7.9 million Distributed Denial of Service (DDoS) attacks in the first half of 2023, representing a 31% year-over-year increase. As 5G adoption gains momentum, the problem will get far worse, requiring more sophisticated DDoS detection/mitigation mechanisms," according to Anand Dutta, Head of Cyber Security Solutions and Presales at Tech Mahindra.
Examples:
Let's look at some of the most eye-opening attacks in recent history. It is public knowledge that there have been massive DDOS attacks in the last few years. These attacks targeted various important business and government sectors and industries. As per the Verizon Enterprise Services security report of 2019, LDAP is used for user authentication, DNS is used to resolve the names of websites, and NTP is used for clock synchronization across the globe. These are the three most attacked services by DDoS due to the nature of impact they can create on major critical services.
On 21st October 2016, Dyn—a company that provides Domain Name System (DNS) services—was a victim of two complex and well-planned DDoS attacks. This was considered to be one of the biggest attacks planned to disrupt the global internet service. The attack was planned to take down data centers all over the globe. Dyn's service takes human-readable internet URL addresses such as www.amazon.com and resolves them into associated IP addresses. Imagine the impact of such a complex DDOS attack on Dyn, which prevented customers from reaching 1200 domains like Amazon, Twitter, New York Times, etc. Now, let's look at some details of the attacks. The attack was noticed by the initial bandwidth elevation on Dyn's managed platform in several regions of Asia Pacific, the United States, and Europe. The attack vector soon changed to a huge volume flood of TCP and UDP packets. These were destined for port 53, originating from a large source of IP addresses. It was later analyzed that 100,000 malicious endpoints were included in the attack. These endpoint devices were IOT devices like Cameras, DVRs, and other unknown devices that were part of botnets—a significant volume of traffic originated from Mirai-based botnets. These botnets consist of Internet of Things (IoT) devices. What is Mirai? Mirai is a piece of malware that infects and exploits the network devices on the internet; in most cases, IoT devices like Printers, Cameras, Scanners, etc., can be used as a botnet in large-scale network attacks. Analysts noted a magnitude of 1.2Tbps range for the Dyn attack. This Dyn attack surely opened up an important issue around device vulnerability and internet threats.
"With the trend toward weaponizing vulnerable IOT devices, there is a noticeable change in the attack landscape. Attackers no longer rely solely on IP spoofing for large-scale attacks as they now have millions of potential weapons that are extremely well connected with fully capable network stacks," according to Rajkumar Jalan, former Chief Technology Officer at A10 Networks.
An anonymous group, later known as the New World Hacking group, launched a DDOS attack against the business and presidential campaign sites of President Donald Trump on April 1, 2016. The attackers sought to damage Trump's brand by taking down the billionaire's website for his hotel chain, email servers, and presidential campaign. [Ref 6.15]
On November 8th, 2017, Boston Globe suffered a DDOS attack. This prevented many of its employees from doing their work and rendered its website inaccessible. It also affected its newspaper's telephones and editorial systems. [Ref 6.16]
![Figure 1 ZDNet statistics on DDoS attacks [Ref – 6.1]](https://d.techtimes.com/en/full/441493/figure-1-zdnet-statistics-ddos-attacks-ref-61.png?w=694&f=934a45d37509b7f1d0605ffb1840eadc)
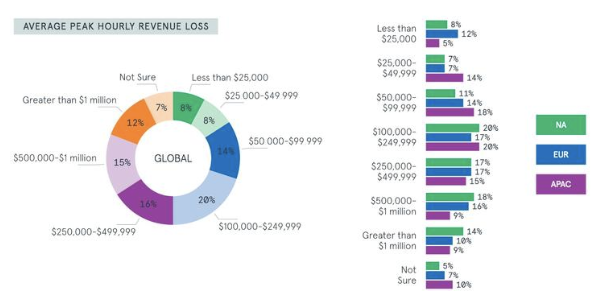
It is important to note how much loss a business has to incur when hit by a DDOS attack. Below is an average peak hourly revenue loss for a DDOS victim.
3. Growth and Trajectory
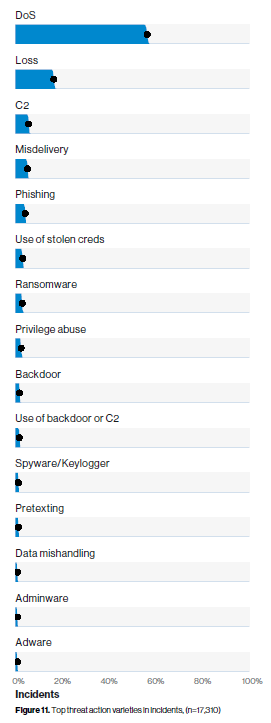
As per Verizon's 2019 Data Breach Investigations Report, an examination of threats and threat actions or types of threats revealed that DDOS is at the top of the attack types or varieties associated with security incidents.
"Protecting data is now a top priority to most organizations. DDOS, by far, has been the most dangerous attack as its bandwidth and impact could go beyond expectation. Nearly two-thirds of the attacks are targeted towards communication service providers. DDOS is a big threat to the telecom industry and can break down a country's communication network in mere minutes, which can bring an entire nation and its emergency response systems to its knees," says Mr. Keshav Kamble, Chief Executive Officer of Avocado Systems. "Multiplication of attacks including derivatives of Mirai attack can lead to Weapons grade DDOS. Our nation needs to be proactive and take appropriate measures towards protecting our society and citizens from this deadly weapon—DDOS," cautions Mr. Kamble.
4. Weapons Grade DDOS, Effects
The objective of this article is not to compare the capabilities of an outcome but to understand preparedness for catastrophic events. The point of view also highlights the fact that in comparison to the traditional weapon's cost and capabilities ratio, DDOS weapons supersede drastically. As per RAND, 1994, pp. 101-132, for any country, the military capabilities can be compared in an intellectual sense by the following factors:
Defense Budget: Total size and % of GNP (Gross National Profit), distribution per service.
Combat RTD&E: Number and distribution by type and service, quality relative to peers.
Man Power: Absolute size of pool, educational and technical proficiency by rank.
Defense Industrial Base: Total number of facilities, sufficiency relative to service need.
Military Infrastructure: Total number of facilities, distribution by category, and service need.
Inventory and Support: Size and structure of inventory, holdings of high leverage systems, sufficiency of logistics.
By some estimates, stocking and upkeep of modern nuclear weapons costs about $20 Billion per year to the United States Department of Defense. The number may vary from country to country, but it certainly is not a trivial cost.
Again, comparing traditional military capabilities, making them effective and upkeep is a huge challenge to most developed countries. Moreover, it has always been a catch-up game without end. All these factors clearly point to the fact that for any military superiority, DDOS weapons are the best, have the lowest cost, are highly and easily scalable, are difficult to trace, have very low manpower, and are easy to develop and maintain capabilities. Countries with a highly developed digital infrastructure, like the United States, are the most vulnerable but, at the same time, are best placed for the development capabilities as well.
In one of the studies done at Avocado Systems labs, it was found that a large number of attacks on their IT infrastructure originated from remote places or rural areas of countries that were not considered to be the first suspects. This clearly points out that those endpoints were portable devices or mobile phones that the attackers networked to use for coordinated attacks.
For DDOS to be weapons-grade, it requires bandwidth. The bandwidth can be the sum of all individual sources used in the process. Therefore, one can use a large number of mobile or portable computer devices for bandwidth aggregation or, worst of all, hack into large bandwidth sources like telecommunication gateways, satellite systems, and intercontinental oceanic fiber optic cable relays to put together a very high aggregate bandwidth.
5. Conclusion
Clearly, one can see that DDOS can be pretty disastrous and can cause severe harm to businesses and infrastructure. Below are a few generic recommendations for DDOS mitigation that can help mitigate the impact of an attempted DDOS attack.
Constantly monitor your DNS and use resilient infrastructure.
Understanding your critical assets and services
Understand how your users connect to your network
Following DDOS protection best practices
Build an organization-wide business continuity plan against DDoS
Artificial Intelligence (AI) can play a significant role in mitigating Distributed Denial of Service (DDoS) attacks by providing advanced threat detection and response capabilities. Here are several ways in which AI can help in this regard:
Traffic Anomaly Detection: AI-based systems can continuously monitor network traffic and identify patterns and anomalies. When the system detects a sudden and abnormal surge in traffic, it can trigger alerts and take preventive actions to block or divert the malicious traffic.
Behavior Analysis: AI can analyze the behavior of network traffic and distinguish between legitimate and malicious traffic. By learning the typical patterns of network behavior, AI systems can identify deviations that are indicative of a DDoS attack.
Real-Time Mitigation: AI can respond to DDoS attacks in real-time. When an attack is detected, AI-based security solutions can automatically adjust network configurations, redirect traffic, or apply rate limiting to mitigate the impact of the attack.
Machine Learning Models: Machine learning models can be trained on historical DDoS attack data to predict and recognize new attack patterns. These models can adapt and evolve as attackers develop new strategies.
Botnet Detection: DDoS attacks often involve the use of botnets, which are networks of compromised devices. AI can help detect and block botnet traffic by analyzing the behavior of devices on the network and identifying unusual patterns.
Cloud-Based DDoS Protection: Many cloud service providers offer AI-driven DDoS protection services that can absorb and mitigate large-scale attacks. These services leverage AI to analyze traffic across their networks and divert malicious traffic away from targeted websites or applications.
User and Device Authentication: AI can assist in user and device authentication to ensure that only authorized users and devices are allowed to access a network or service. This helps prevent unauthorized access that could lead to DDoS attacks.
Predictive Analytics: AI can help predict potential DDoS attacks by analyzing historical data, monitoring emerging threat trends, and assessing the security posture of the network. This proactive approach allows organizations to take preventive measures in advance.
Intelligent Filtering: AI can be used to intelligently filter and classify incoming traffic based on its source, behavior, and other attributes. This allows legitimate traffic to pass through while blocking or redirecting malicious traffic.
DNS Filtering: AI-driven DNS filtering can help prevent DNS amplification attacks, which are a common DDoS vector. By identifying and blocking DNS requests that exhibit attack characteristics, AI can reduce the impact of such attacks.
It's important to note that AI is not a silver bullet, and DDoS mitigation should be part of a comprehensive cybersecurity strategy that includes network architecture design, intrusion prevention systems, load balancing, and incident response plans. AI should complement these measures to enhance security and response capabilities.
6 References
6.1 https://www.zdnet.com/article/the-average-ddos-attack-cost-for-businesses-rises-to-over-2-5m/
6.2 https://www.netcraft.com/blog/bbc-websites-still-suffering-after-ddos-attack/
6.3 https://www.nist.gov/programs-projects/advanced-ddos-mitigation-techniques
6.4 https://www.teskalabs.com/blog/how-ddos-can-sink-your-business
6.5 https://www.cisa.gov/cybersecurity-toolkit-and-resources-protect-elections
6.6 https://www.cisecurity.org/insights/white-papers/ms-isac-guide-to-ddos-attacks
6.7 https://www.nti.org/analysis/articles/us-nuclear-weapons-budget-overview/
6.8 https://fas.org/rlg/wmd-2018.pdf
6.9 https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-189.pdf
6.10 https://www.brookings.edu/opinions/maintaining-our-nuclear-arsenal-is-expensive
6.11 https://www.rand.org/content/dam/rand/pubs/monograph_reports/MR1110/MR1110.ch7.pdf
6.13 https://www.dhs.gov/science-and-technology/ddosd
6.14 https://www.netscout.com/blog/ddos-attacks-against-governments-are-rise
6.16 https://www.studypool.com/documents/11753694/boston-globe-attack
6.17 Verizon Security Report 2018, 2019.

ⓒ 2025 TECHTIMES.com All rights reserved. Do not reproduce without permission.




