In today's rapidly evolving identity landscape, organizations are accelerating their adoption of cloud-first strategies (specifically by modernizing identity infrastructure through the adoption of cloud-based Microsoft identity providers) and implementing Zero Trust Architecture at an unprecedented pace. As these transformations unfold, the demand for user-friendly authentication and seamless, secure access to resources managed by Microsoft identity providers on Windows has intensified. Microsoft's Web Account Manager (WAM) has quietly emerged as a foundational pillar for secure access across Windows platforms, meeting these demands with robust efficiency. Originally introduced with Windows 10, WAM (either directly or through MSAL integration with WAM) now powers single sign-on (SSO) experiences for millions of users across flagship applications such as Microsoft 365 Copilot, Microsoft Office 365, Microsoft Teams, OneDrive, and a wide range of other Windows applications. By contrast, traditional authentication methods often resulted in fragmented user experiences, increased developer overhead, and potential security vulnerabilities. WAM addresses these challenges by centralizing identity management and token handling, thereby enabling application developers to deliver consistent, secure, and frictionless authentication for end users. This article examines the operational principles of WAM, its multifaceted benefits for users, developers, and organizations, and its critical role as an enabler of Zero Trust security and modern identity and access management within the Microsoft ecosystem.
The Fragmentation Problem: The Case for WAM
Windows applications integrating with Microsoft identity providers without using any of the Microsoft-owned authentication libraries will be characterized by architectural and operational fragmentation that imposes costs on developers, introduces security variability, and degrades user experience. Applications implementing their own OAuth 2.0 and OpenID Connect (OIDC) protocol flows, managing token caches independently, and designing idiosyncratic sign-in interfaces produce several interrelated challenges:
- Protocol and integration complexity
- Each application must independently master the intricacies of OAuth 2.0/OIDC endpoints exposed by Microsoft Identity Providers, the different grant types, token acquisition patterns, refresh semantics, and robust error handling.
- Ongoing protocol evolution and Microsoft identity provider-specific nuances necessitate a dedicated identity engineering capability to track changes and retrofit implementations across app portfolios.
- Microsoft identity provider's documentation gaps amplify integration difficulty, yielding uneven quality and duplicated effort across teams.
- Token caching and lifecycle management
- Applications rolling their own token caches and lifecycle logic (expiry, revocation) lead to divergent behaviors and reliability issues.
- Variability in storage and protection practices for tokens increases the risk surface for credential exposure.
- Security and compliance risks
- Inconsistent token caching and protection (e.g., storage location, encryption, access controls) undermine uniform enforcement of security baselines.
- Inconsistent token lifecycle management complicates incident response and reduces the auditability and traceability necessary for compliance programs.
- User friction and inconsistent experience
- Users encounter repeated and unnecessary sign-ins across apps and services due to the absence of Single Sign-On, thereby degrading user productivity.
- Varied prompts, consent flows, and UI patterns across applications create cognitive load, erode user trust, and increase support burden.
- Operational overhead and scalability constraints
- Teams bear ongoing maintenance costs to keep pace with identity protocol updates, diverting resources from core product features.
- Duplicating identity logic across multiple applications erodes economies of scale and amplifies support overhead. Each application must maintain specialized expertise in its bespoke identity stack, resulting in fragmented support structures and significantly higher operational costs for the organization.
- Fragmentation hinders centralized governance, prevents uniform enforcement of security and compliance policies, and slows the deployment of identity-related enhancements.
Foregoing a Microsoft-authored authentication library externalizes protocol complexity to every application, propagates security variability through bespoke token handling, and fragments the end-user experience. These outcomes collectively motivate a system-level approach that centralizes account and token management, standardizes user experience, and enables seamless SSO; objectives that authentication libraries such as WAM are designed to address.
From Fragmentation to Centralization: WAM
WAM is a core component of the Windows platform. It serves as an authentication library that enables seamless Single Sign-On (SSO) by brokering token acquisition (and all aspects of it) between Windows applications and Microsoft cloud identity providers such as Microsoft Entra ID (formerly Azure Active Directory) and Microsoft Account, using modern identity and access management protocols.
Key Benefits of WAM Organized by Stakeholders
End Users
- Seamless Single Sign-On (SSO): WAM is deeply integrated with Windows, using the user's current session and SSO artifacts (like Primary Refresh Tokens and Device Credentials) to deliver effortless SSO across applications. This streamlines access and boosts productivity.
- Consistent Identity Experience: Users enjoy a unified authentication and authorization process across all Windows apps, resulting in a smoother and more predictable experience.
Application Developers
- Simplified Integration: WAM abstracts the complexities of implementing OAuth 2.0 and OpenID Connect flows with Microsoft identity providers, simplifying integration for application developers. This allows developers to focus on core application functionality rather than identity management.
- Centralized Token Management and Protection: WAM handles token acquisition, caching, and lifecycle management, significantly reducing developer effort and minimizing security risks associated with inconsistent or insecure token storage.
- Built-In Security & Future Readiness: Security and reliability are handled by WAM, so developers don't need deep protocol expertise. As new security and identity features are released, they're delivered automatically to the applications, minimizing maintenance and ensuring applications stay protected and compliant.
- Modern Identity and Access Management Standards Support: WAM supports advanced security features like Token Binding, Proof of Possession (PoP) tokens, and phishing-resistant credentials (e.g., Windows Hello, FIDO2). By working with Microsoft Entra ID, WAM ensures refresh tokens are device-bound and protected, preventing misuse even if credentials are compromised.
Organizations
- Zero Trust and Compliance: WAM enables device registration and mobile device management (MDM) enrollment, empowering organizations to manage devices and enforce compliance via MDM providers like Microsoft Intune. It also supports Conditional Access policies through Microsoft Entra ID, ensuring only trusted users from compliant devices can access resources. This makes WAM a cornerstone for Zero Trust security and enterprise-grade compliance.
- Comprehensive Feature Support: Applications using WAM can natively leverage enhanced security features like Windows Hello, Conditional Access, and FIDO keys, ensuring that organizational policies are consistently applied and enforced across all client applications.
WAM Token Request API Overview
WAM provides two main WinRT APIs for token acquisition:
- GetTokenSilently – Attempts silent token retrieval without user interaction. If it fails, it does not fall back to interactive methods.
- RequestToken – Tries silent retrieval first; if it fails with an interaction_required error, it initiates an interactive flow.
These APIs support integration across languages like C#, C++, and VB.
Token Request Workflow
1. Identify the WebAccountProvider: Applications must first specify the identity provider:
- Microsoft Entra ID: FindAccountProviderAsync("https://login.microsoft.com," authority)
- Microsoft Account: FindAccountProviderAsync("https://login.live.com," authority)
This step ensures WAM routes the request to the correct plugin (AAD or MSA).
2. Construct the Token Request
Use the provider from the first step and create a WebTokenRequest: WebTokenRequest(provider, scope, clientId)
3. Request the Token
- Silent: GetTokenSilentlyAsync(request) – Ideal for background apps.
- Interactive: RequestTokenAsync(request) – Supports prompt types:
- Default: Silent first, then prompt.
- ForceAuthentication: Always prompt.
Essential Security Artifacts to Understand Before Exploring the WAM Token Request API
1. Session Key: A symmetric key bound to the device, used for:
- Proof-of-Possession (PoP): Signs token requests when using grant_type=jwt-bearer.
- Token Encryption: Acts as the Content Encryption Key (CEK) in JWE responses from Microsoft Entra ID.
2. Device Transport Key: An asymmetric key pair registered with Microsoft Entra ID. The public key encrypts the session key before it's sent to the client.
3. Primary Refresh Token (PRT): A device-bound opaque token issued post-authentication. It contains the session key and enables SSO. PRTs are validated by proving possession of the embedded session key.
DeepDive: GetTokenSilently
The GetTokenSilentlyAsync API in WAM enables secure, silent token acquisition on Windows devices. This deep dive explores the different device states that govern its behavior and the security underpinnings.
Device State and WAM GetTokenSilently API Behavior
Microsoft Entra Joined
When a device is Microsoft Entra Joined and a user successfully signs in with Entra ID credentials, Microsoft Entra ID issues a Primary Refresh Token (PRT) along with a Session Key. This information is securely stored by LSASS (Local Security Authority Subsystem Service).
WAM first attempts to acquire a token using the Refresh Token. If that fails, it falls back to using the PRT.
Microsoft Entra Hybrid Joined
Similar to Microsoft Entra Joined, but adds fallback to Windows Integrated Authentication (WIA) if requesting a token using both RT and PRT fails.
Domain Joined
No PRT is available. WAM attempts WIA directly unless a WebAccount is provided associated with a cached RT.
Security
Silent Token Request using Primary Refresh Token
PRT is bound to the device using the session key, and WAM must show Proof-Of-Possession by signing the grant with the same session key as the one within the PRT. Entra ID will validate the signature by verifying if the grant is signed using the same session key as the one in the PRT. Once Entra ID is done verifying the signature, it will authenticate the user and the device using the information from the PRT and then issue an Access Token and a new PRT.
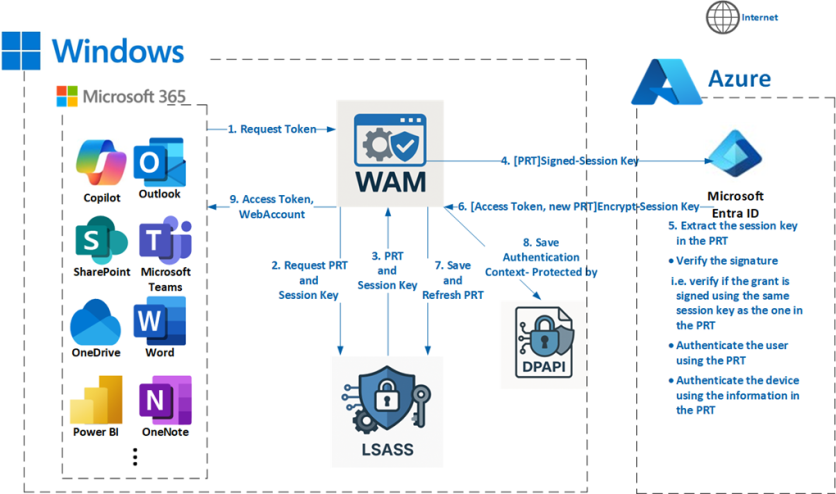
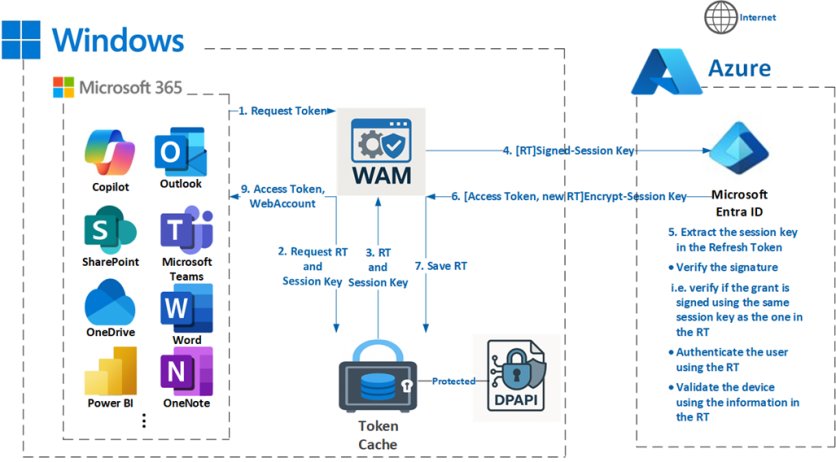
Silent Token Request Using Refresh Token
Similar to PRT flow. RT is also device-bound and signed with the session key. Entra ID returns a new Access Token and RT, which is stored securely using DPAPI.
Deep Dive: RequestToken
When applications request tokens using the WAM API, they may occasionally trigger interactive authentication prompts from Microsoft Entra ID. This typically occurs when:
- The silent token request uses an SSO artifact (e.g., RT, PRT, SAML assertion) that lacks an MFA claim.
- A Conditional Access (CA) policy enforces periodic MFA (e.g., every 24 hours or once every week).
If silent acquisition fails, RequestTokenAsync follows the OAuth 2.0 Authorization Code flow (RFC 6749, section 4.1).
Token Request Flow: Microsoft Entra Joined & Microsoft Entra Hybrid Joined Devices
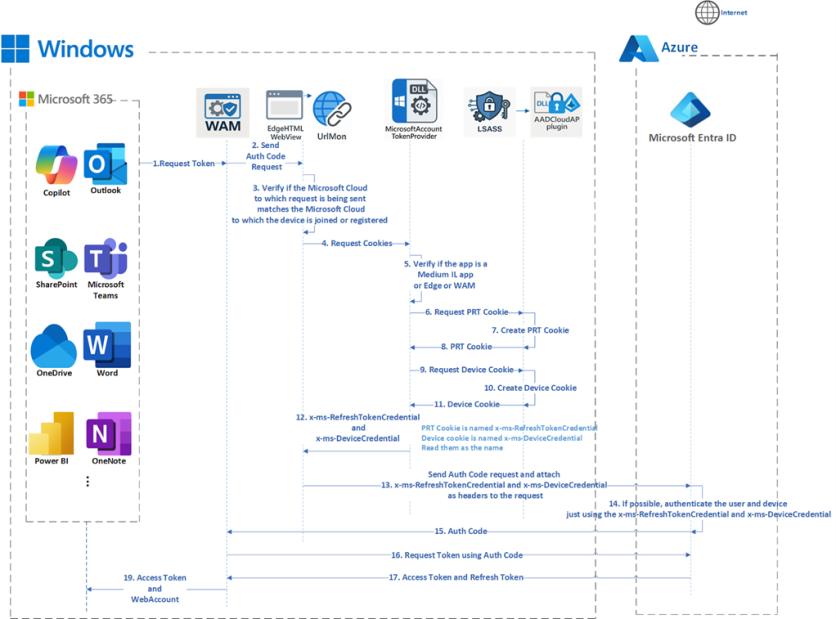
1. Token Request Initiation: The application requests an access token via WAM.
2. Auth Code Request: WAM constructs and sends an auth code request using WebView1 (embedded browser).
3. Cloud Verification: UrlMon intercepts the request, extracts the host, and verifies if it matches the Microsoft Cloud the device is joined to.
4. SSO Artifact Request: If matched, UrlMon calls ProofOfPossessionCookieInfo to request:
- x-ms-RefreshTokenCredential (PRT cookie)
- x-ms-DeviceCredential (device SSO cookie)
5. Validation: MicrosoftAccountTokenProvider ensures the request originates from WAM, Edge, or a Medium-IL app.
6.7. 8. PRT Cookie Retrieval from AADCloudAuthenticationPackage Plugin:
- If cached and valid, reuse it.
- Otherwise, generate a new JWT payload with the PRT and sign it with the session key (HMAC-SHA256).
9.10. 11. Device SSO Cookie Retrieval from AADCloudAuthenticationPackage Plugin:
- If cached and valid, reuse it.
- Otherwise, generate a new JWT payload and sign it with the device certificate (RSA-SHA256).
13. SSO Headers Attachment: UrlMon attaches the PRT and Device SSO cookies as headers to the auth code request being sent to the authorize endpoint.
14. Authentication: Entra ID authenticates the user and device using the SSO headers.
15. Auth Code Issuance: Upon successful authentication, Entra ID returns an auth code to WAM.
16. Token Exchange: WAM uses the auth code to request an access token and a refresh token from Entra ID.
17. Token Issuance: Entra ID validates the auth code and issues:
- Access Token
- Refresh Token (device-bound, signed with the session key)
18. Token Caching: WAM caches the refresh token, protected by DPAPI.
19. Token Delivery: WAM returns the access token and a WebAccount to the application.
This flow ensures secure, seamless token acquisition while respecting conditional access policies and device trust states.
Future Enhancements
- Enhancing the Token Binding Strategy: Existing token protection strategies, such as Access Token Proof of Possession (AT PoP) and Refresh Token Proof of Possession (RT PoP), are insufficient to defend against zero-day attacks, where a highly privileged attacker could exploit vulnerabilities. For instance, an attacker might steal a token from cache if the binding key is stored in software or obtain a new token using a binding key under their control. To provide robust protection against zero-day threats, the token binding strategy must be enhanced to ensure that token binding keys (and, by extension, the tokens themselves) are securely tied to the device and cannot be misused elsewhere.
Conclusion
In summary, the Web Account Manager (WAM) stands as a pivotal innovation within Microsoft's identity platform, fundamentally transforming how authentication and access are managed across the Windows ecosystem. By abstracting the intricate details of OAuth 2.0 and OpenID Connect protocols, WAM not only streamlines the integration process for developers but also ensures that security and compliance are maintained at an organizational level. Its architectural design (centered on centralized token and account management, device-bound credentials, and Proof-of-Possession mechanisms) embodies the principles of Zero Trust, thereby mitigating risks associated with fragmented identity solutions and inconsistent security practices.
WAM's seamless support for both silent and interactive token acquisition, coupled with its deep integration with Windows and Microsoft Entra ID, enables organizations to deliver consistent Single Sign-On (SSO) experiences while enforcing advanced security policies such as Conditional Access. This dual focus on usability and security positions WAM as an essential enabler for organizations pursuing cloud-first, secure-by-design strategies in an increasingly complex identity landscape.
As the demands on identity infrastructure continue to evolve, driven by the proliferation of devices and the escalating sophistication of cyber threats, WAM's adaptability and extensibility ensure that it remains a future-proof solution. Ultimately, WAM not only addresses the immediate challenges of modern authentication but also lays a resilient foundation for the next generation of secure, user-, developer- and organization-centric identity and access management.
References
- D. Hardt, "The OAuth 2.0 Authorization Framework," RFC 6749, IETF, Oct. 2012. [Online]. Available: https://www.rfc-editor.org/rfc/rfc6749
- N. Sakimura, J. Bradley, M. Jones, B. de Medeiros, and C. Mortimore, "OpenID Connect Core 1.0," OpenID Foundation, Nov. 2014. [Online]. Available: https://openid.net/specs/openid-connect-core-1_0.html
- J. Bradley, H. Tschofenig, and N. Sakimura, "Proof-of-Possession Key Semantics for JSON Web Tokens (JWTs)," RFC 7800, Internet Engineering Task Force (IETF), Apr. 2016. [Online]. Available: https://datatracker.ietf.org/doc/html/rfc7800
- Microsoft Documentation: WebAuthenticationCoreManager
- NIST, "Zero Trust Architecture," NIST Special Publication 800-207, Aug. 2020. [Online]. Available: https://doi.org/10.6028/NIST.SP.800-207
ⓒ 2026 TECHTIMES.com All rights reserved. Do not reproduce without permission.




