Intel is currently investigating a security breach after a Swiss software engineer published on Twitter 20 GB of internal files, which include "confidential" and "restricted secret" documents. The files entitled "Intel exconfidential Lake Platform Release ;)" that were uploaded on file-sharing site MEGA are the first of a series of leaks of Intel files.

The data was leaked by Till Kottmann who claimed he received the Intel files from a Telegram channel where he releases leaked data from web portals, cloud servers, and Git repositories of major tech companies. The sender was a hacker who allegedly accessed Intel earlier this year. Kottmann said in his tweet that many of the files "have NOT been published ANYWHERE before."
Tech Radar reported that leaked folders include chip engineering files that were allegedly stolen from Intel earlier this year. These may also contain 'backdoors' to some of Intel's source code as the hacker urges to look for them by giving a sample clip in the original post.
Meanwhile, ZDNet analyzed with security researchers who have previously analyzed Intel CPUs and they deemed the leak authentic. The files Intel intellectual property related to internal various chipsets design as well as technical specs, product guides, and manuals for CPUs which dated back to 2016.
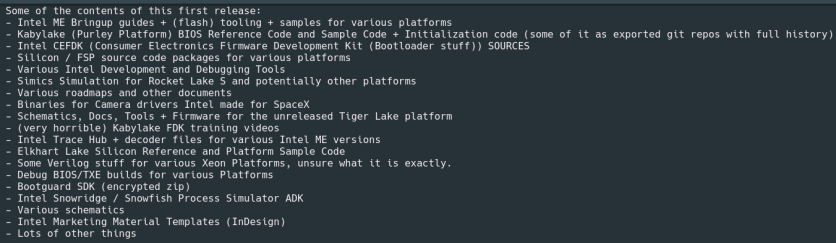
Kottman even noted that password-protected zips may be accessed using password "Intel123" or "intel123." The passwords were already set up when the files were accessed.The following is a list of files included in the leak.
- Kabylake (Purley Platform) BIOS Reference Code and Sample Code + Initialization code (some of it as exported git repos with full history)
Intel ME Bringup guides + (flash) tooling + samples for various platforms
Intel CEFDK (Consumer Electronics Firmware Development Kit (Bootloader stuff)) SOURCES
Various Intel Development and Debugging Tool
Silicon / FSP source code packages for various platforms
Binaries for Camera drivers Intel made for SpaceX
Schematics, Docs, Tools + Firmware for the unreleased Tiger Lake platform
Simics Simulation for Rocket Lake S and potentially other platforms
Various roadmaps and other documents
(very horrible) Kabylake FDK training videos
Some Verilog stuff for various Xeon Platforms, unsure what it is exactly.
Debug BIOS/TXE builds for various Platforms
Intel Trace Hub + decoder files for various Intel ME versions
Elkhart Lake Silicon Reference and Platform Sample Code
Intel Snowridge / Snowfish Process Simulator ADK
Bootguard SDK (encrypted zip)
Various schematics
Intel Marketing Material Templates (InDesign)
While the cybercriminal did not include information of Intel customers or employees, it is quite worrying as to what other files the hacker could access. Intel initially said
Read also: How to Easily Password Protect a PDF from Data Breach
Intel's response on the breach
In an email statement sent to ZDNet, Intel said they "are investigating this situation." The company also disputed Kottman's claim about the hacking of the chip-maker's system.
Instead, it implied that staff might have shared the confidential data after illegally downloading it from Intel Resource and Design Center (IRDC), a web portal that hosts Intel's technical documents shared with business partners. "We believe an individual with access downloaded and shared this data," Intel said.
While many of the leaked data contained links to the IRDC, the alleged hacker claimed to have accessed the data through an unsecured server hosted on Akamai CDN. This was based on a copy of the chat between Kottmann and the hacker that was obtained by ZDNet.
Regardless of how the data was acquired, Intel should act fast as the hacker is inclined in releasing more files in the future.





